005#:THM - TShark Challenge II: Directory

Here we have the second in the TShark Challenge series from TryHackMe. The first one was a quick exercise so I figured I would tackle this one as well. The premise is that “a user came across a poor file index, and their curiosity led to problems”. They also mention we will be working with DNS queries as well as using TShark and VirusTotal again. Let’s use what we learned from the last room and use the -Y switch to filter by HTTP traffic. This didn’t give me anything useful, so I adjusted the parameters to search for DNS traffic instead.
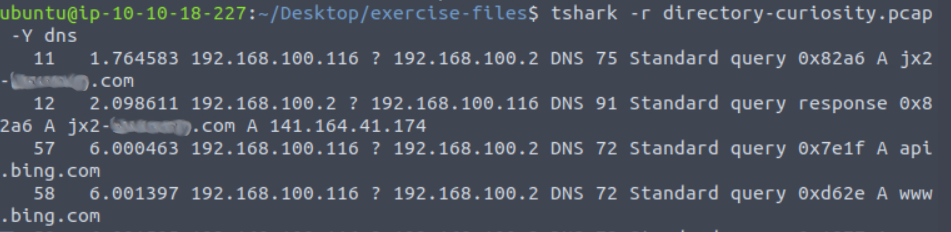
The first result we get happens to be our malicious domain. Once we defang the link using CyberChef we are left with our first flag.
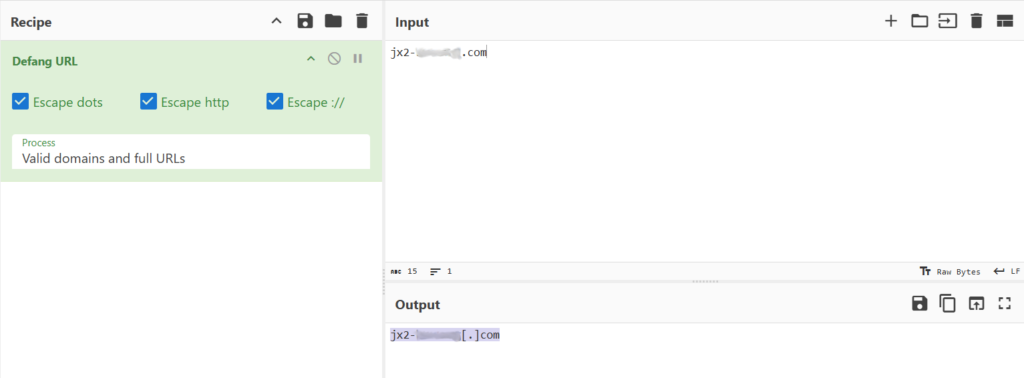
The second flag asks us to find the total number of HTTP requests to this specific domain. I haven’t used TShark much, so I began by just referring to its help documentation. I didn’t notice anything good for right now. Wireshark allows you to follow a conversation easily so I figured TShark would be capable of something similar. I decided to pull up the man page and start working through that. Eventually we stumble across the -z switch which deals with statistics.
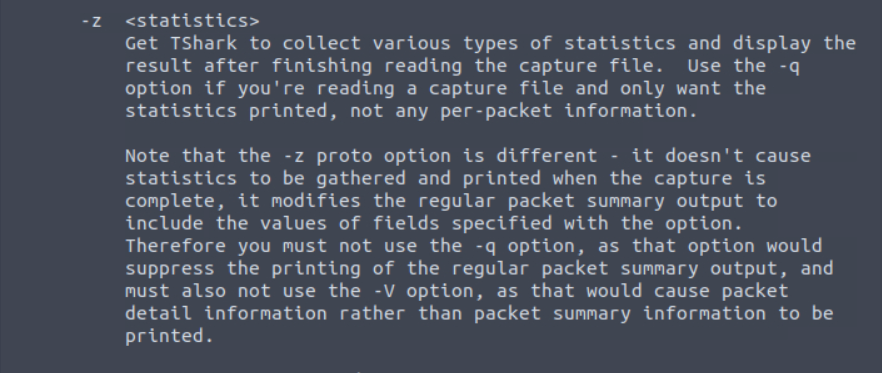
I also took note of the -q switch they mention to limit the output to just the statistics. There happens to be a ton of options to use with -z so I spent a some time trying a few commands before finally landing on one that gave me the second flag.
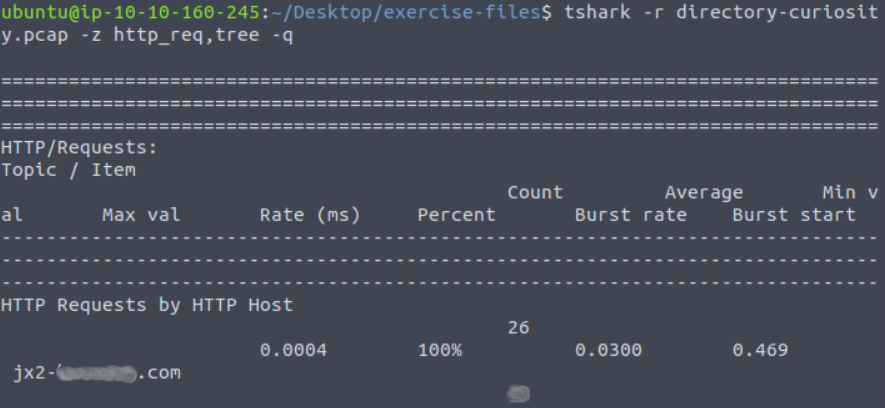
Running the output of directory-curiosity.pcap through grep quickly gets us the third flag. You will need to defang it using CyberChef’s IP Addresses filter first though.
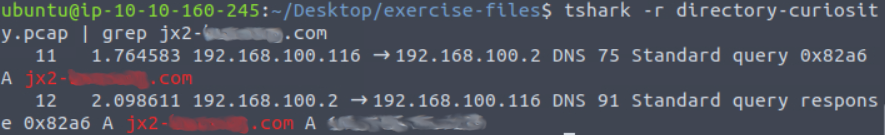
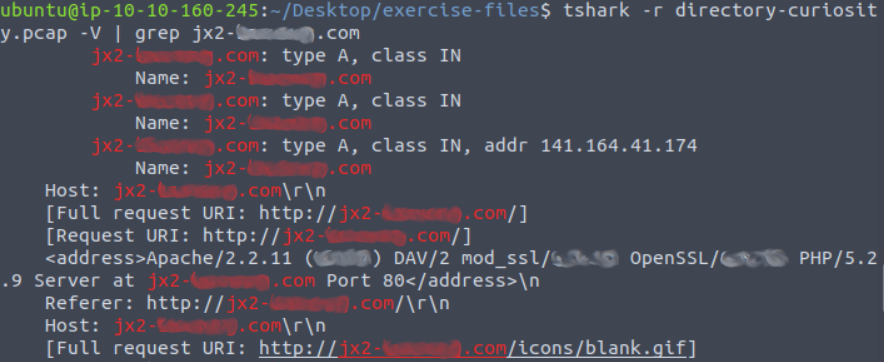
To get the server info for flag 4 I reran my grep command with the -V switch to search the contents of the packets too.
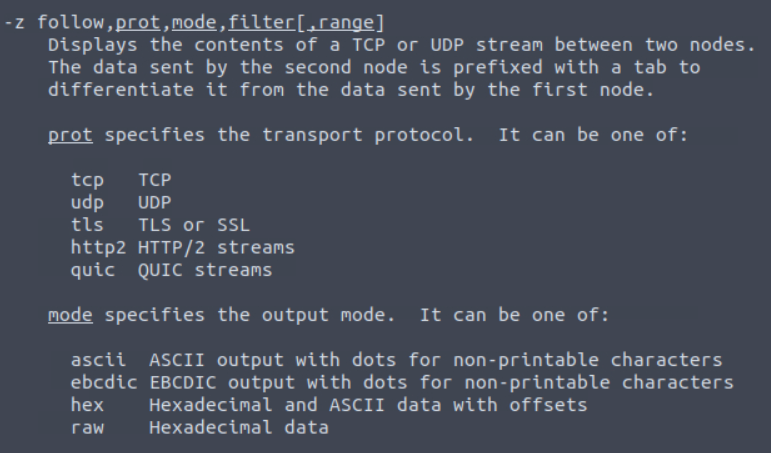
Next, we are asked to “Follow the ‘first TCP stream’ in ‘ASCII'”. I’m not sure how to do that so I again refer to the manual page for TShark. It looks like we can use ‘-z follow’ for this flag. At first, I had run it against position 1 since we want to follow the “first” TCP stream. This didn’t give me the answer though. After some reflecting it occurred to me that the first position would actually be 0 instead of 1. Rerunning the command and we are able to gather the fifth flag by counting the files listed.
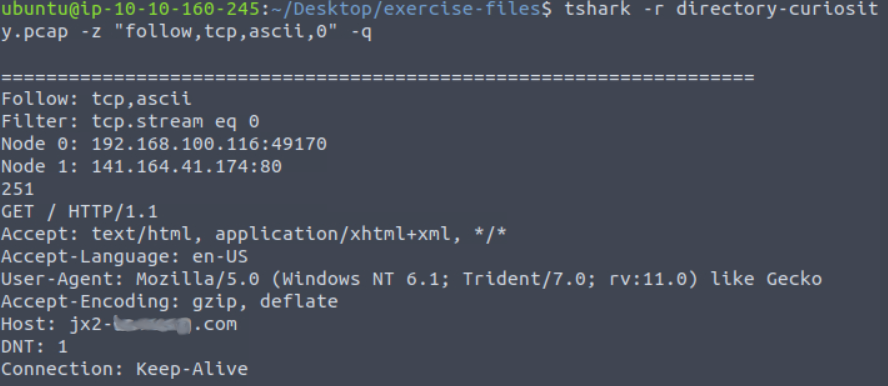
The sixth flag is the name of the first file defanged. For this you just put square brackets [ ] around the period in the file name. Same for flag seven but with the exe file. The next question asks us about the SHA256 value of the malicious file.
At this point, I jumped over to VirusTotal and searched the malicious domain before looking over the Relations tab. This pane includes info about related files and we see vlauto.exe in the list. Clicking the link for that file got me it’s SHA256 but this turned out to be incorrect. Also, looking ahead to the next question they are prompting us to go to VirusTotal, so the hash I need must be in the packet capture.
I tried a few modified versions of commands I had run before but nothing was working. I decided to refer back to the manual again and towards the bottom found something promising.
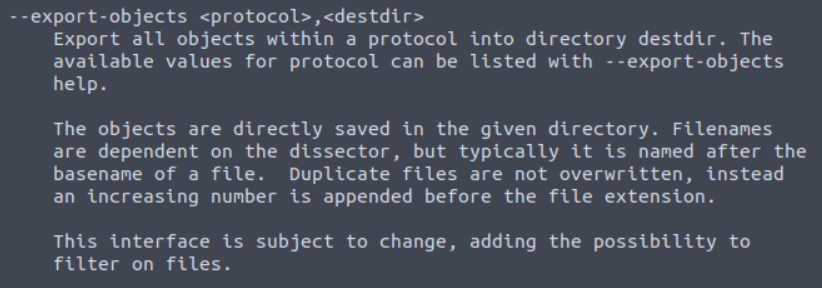
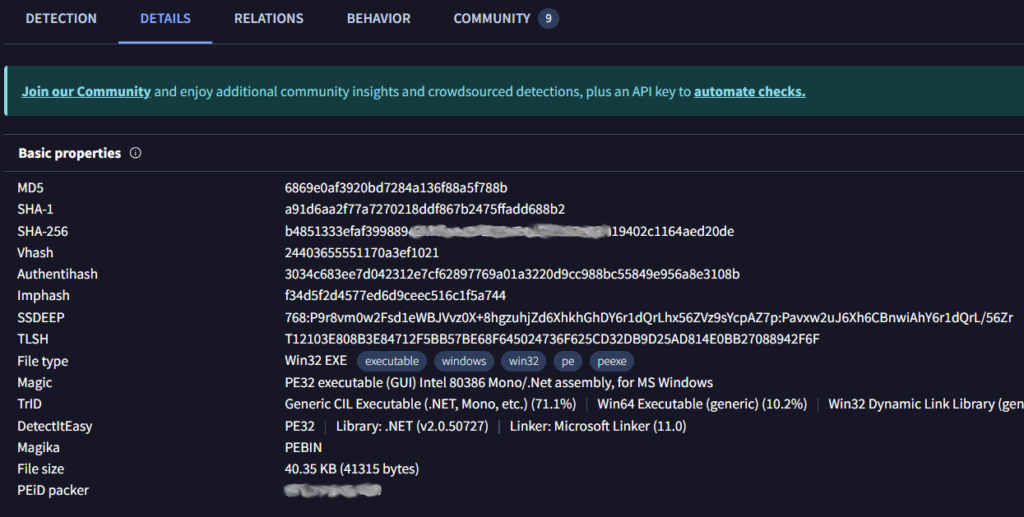
I tried using this command to export files related to HTTP traffic in the pcap to my current directory. This worked and is a pretty cool feature I wasn’t aware of. It turns out this is also possible with WireShark, I just haven’t used it. Here is a good article by Palo Alto Networks threat research team, Unit 42. Since we now have copies of the files, we can get the SHA256 of vlauto.exe.
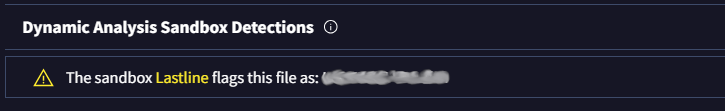
Jumping over to VirusTotal to search this hash we can find flag eight under the Details tab. For the final flag we can look at the Behavior tab.
[CATZ….HACKS]