007#:HTB - Keeper

The next room on my list is Keeper on Hack the Box. Skimming over the description for the room, I see that we will be attacking a ticketing system then pivoting to accessing it through SSH. As always, I begin with a nmap scan.
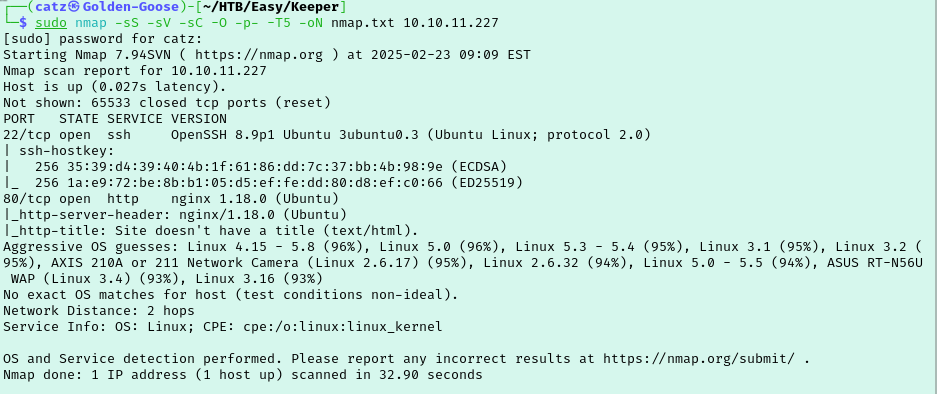
Since we see that port 80 is open, I get a gobuster scan going and pull the site up in my web browser.

Gobuster didn’t give us anything useful but in our web browser we can see they reference tickets.keeper.htb. I add both the domain and subdomain to my hosts file.

Clicking the link on the site takes us to a login portal where we gather that it is running something called Request Tracker 4.4.4+dfsg-2ubuntu1. I checked this in searchsploit and for vulnerabilities on google. I looked through the source code before successfully logging in using the default credentials for Request Tracker’s root account.
Once in, I just started clicking around to see what I could find. I quickly stumbled on a ticket where I get some additional usernames and a URL to try. I created a new file named users.txt and added each one I saw. I also tried visiting the URL and played around with the number in the link but I didn’t find anything.
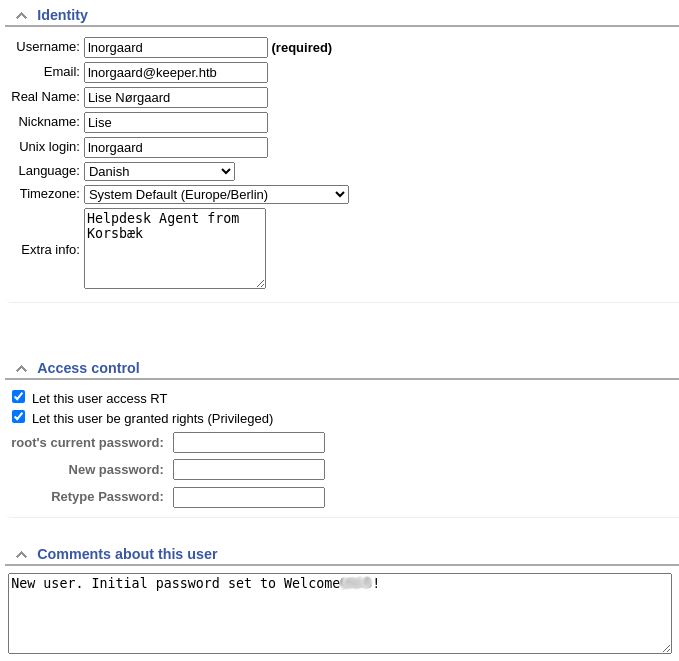
I continued working my way through what I could access when I discovered I could edit lnorgaard’s account. In the edit screen for this user we see a comment containing their password.
I logged in as lnordgaard but their dashboard is in another language so I am not able to do much. I decided to try lnorgaard’s credentials against SSH. We are in! Right away this gives us our first flag.
I checked the user’s sudo rights and decided to unzip the RT30000.zip file in lnorgaard’s home directory. The ticket we read mentioned that they saved the KeePass dump to their home folder, and after it unzips we can confirm that is what we are working with. I tried to just cat the dmp file at first but there was too much output. I tried using strings but it wasn’t installed so I decided to host a python server and just pull the files to my local machine for further inspection.
There was still too much output, unfortunately. I went to see if I had KeePass installed and stumbled across keepass2john instead. This is interesting so I used the conversion tool and began cracking with John. How long it was taking told me this probably wasn’t right though. I decided to look up how to view KeePass dmp files and the first result was this article which discusses how you can recover most of a password from a memory dump. That article mentions they used a POC from a github repository so I searched for that which landed me on this page.
Following the instructions, I installed .NET and cloned the repository before running it against our .dmp file. This gave me errors that were only resolved by me installing .NET v7. The results aren’t making a ton of sense to me though.
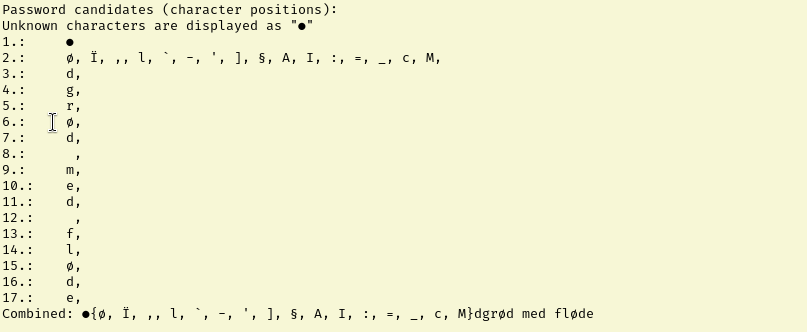
From reading about the POC I know the first character of the password is unknown and it looks like it is telling me the second character could be a handful of things. I assumed this was encoded so I copied letters 3-17 ,”dgrød med fløde”, into dCode’s cipher identifier. Oddly this didn’t flag it as any cipher. At this point I got pretty stuck and turned to answering the guided questions for the room. Task 7’s hint tells us that:
“A web search for the characters it does recover should help identify the full password.”
I took the phrase I had to google and discovered I was actually looking at a partial name of the Danish dish known as rødgrød med fløde. Entering this as the answer to Task 7 confirms that it is the password for our KeePass backup file. Now I just have to figure out how to get into it. After some quick googling I installed KeePassX and tried to open the file.
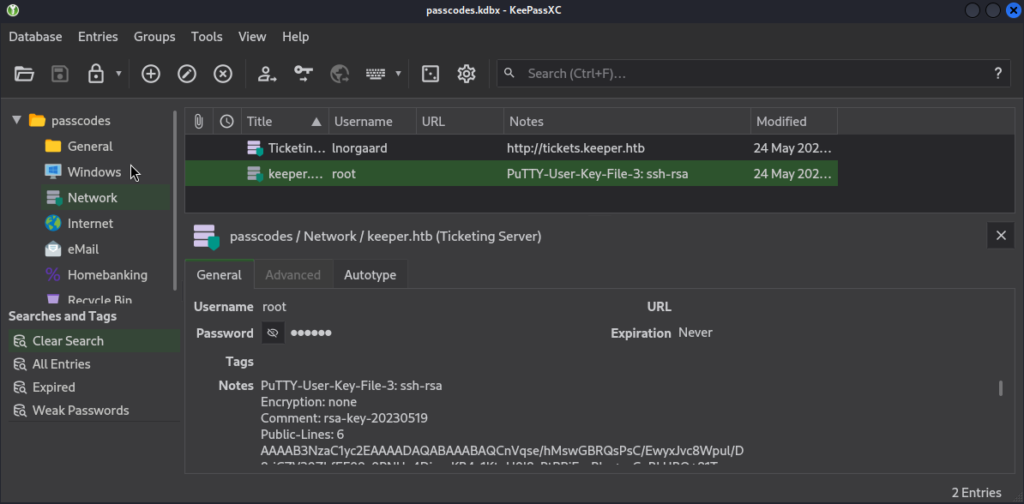
Running keepassxc against the passcodes.kdbx file opened a GUI where we found the credentials for a PuTTY SSH key. I saved the contents of the key to a new file named id_rsa and noted the password for it. I had tried to SSH directly from terminal but I kept having issues. When looking into this I was seeing people suggest converting the key but I opted to just install and run PuTTY right from my Kali machine instead. This gets us in as root and our final flag.