024#:HTB - Beep

Next up we have Beep from Hack the Box. The last room I did was really fun so I’m excited to dive back in this morning. Like usual, we will start off with an nmap scan.

Alright, we have a lot going on here. We seem to be working with a mail server, its hosting a site, running MySQL, and some other stuff. I will start just by getting a gobuster scan going and pulling up the site in my browser.

Neither worked though, so I pulled up metasploit to try some smtp enumeration instead. This didn’t seem to get anything though. There doesn’t look to be an imap enum tool.
At this point I am just searching things in searchsploit and metasploit that I noticed on the nmap results. Tried a Cyrus exploit that failed. Checked for something against Hylafax. Checked for something against Asterisk Call Manager and tried a few but nothing worked. Checked for something against Miniserv, OpenSSH, CentOS and Apache.
At this point I fell back to the Guided Mode questions. Task 2’s hint mentions that if the web page won’t load that I may have to lower the web security of my browser. I absolutely should have caught this as I had gone back to the site a couple times trying to access. What I neglected was to read the error in my browser suggesting the client/server don’t support a common SSL suite. It also looks like the Chromium browser I was using won’t let me downgrade my security.
Back to firefox it is then. I had to google how to enable TLS1.0 in firefox, but after I did I am now able to view the website.

Now that we have that sorted, I got my gobuster scan going again and looked up default credentials for Elastix. Gobuster was still giving me trouble but this time I noticed the error states “x509: certificate has expired or is not yet valid”. I checked the help page for gobuster to see if there is something I can use. Adding the –k switch to our command tells it to ignore the certificate and gets us some results.

The default credentials I found didn’t work so I moved on to checking out the directories we discovered. When I tried to visit /admin the default credentials didn’t work there either, but it did reveal a FreePBX page that tells us the version number. Naturally, we check that in searchsploit and it looks like there is a metasploit module we can attempt.

I tried one exploit that failed. Moved on to checking more directories we found. During this, I noticed we have numerous logon portals at /mail, /recordings, and at /admin so far. Nothing has worked so far and I am at the end of my gobuster list. I revisited the main page and decided to check for any elastix vulns despite not having a version number. When searching elastix in msfconsole I only get one result that is related to FreePBX. Its for enumerating users but I’ve hit a wall at this point so I gave it a shot.

This didn’t work but I was using port 80 so I retired with 443. This failed too though. Expanding my search of exlastix with searchsploit, we have a few more things to try.

I tried the first one on the list, 38078, and it either doesn’t work or I don’t know how to make it work. The next one was 38522 and this looks like it worked!

That was just a test though. Let’s try to do something more substantial. I’m a little rusty on my cross-site scripting attack paths so I looked up ‘xss reverse shell’ and started reading over this article. I was having a good bit of trouble getting this attack to work though. After refreshing myself on the topic with Portswigger’s documentation, I’m not as confident this Is my attack path since it seems like we would mainly be capturing other user’s credentials, but we are the only users here.

Looping back to our searchsploit results, the next one is also a XSS vuln so I’m going to skip that. This brings us to 37637 which is a local file inclusion vulnerability. After commenting out the top section of the payload I can run it with perl. I was getting errors though so I reviewed the payload further and I think I found my mistake (syntax error). Still fails though. Inside the payload, they have the a commented out line that is called LFI Exploit.

I just copied and pasted that into my browser as the directory path and it seems like it worked, so I’m not sure why the perl script didn’t work.

This data is hard to read as is, but if we view the source code it’s much more digestible. Near the top it looks like we have some credentials. This is great, and it looks like they used the same password for at least three accounts in this config which bodes well for us. Using these credentials we can get into two of the three portals from earlier.


Time to poke around and see what we have access to. The /recordings page didn’t have much of value besides the FreePBX version. I’m not seeing anything particularly valuable in either portal besides a user’s name, Fanis Papafanopoulos (cool name). I referred back to the nmap results to see if there was something else I might try to log into. Looks like SSH is open so I give that a shot. This gave an odd error though.

I haven’t encountered this before so I googled the error message. I found a forum that posted this great link to an OpenSSH article about our issue. Basically, we just need to specify that we want to use a depreciated algorithm. Running my modified command I now get a new error I need to search.

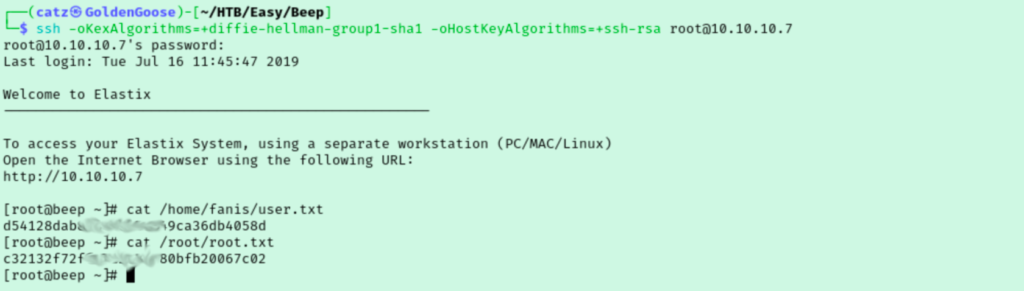
I found the solution and tried both algorithms. I finally got SSH working but I couldn’t log in as admin. I tried asteriskuser but that fails too. Looking over my notes I realized I remembered we found that user with the long name. I tried variations of the first name and last name with no luck. I got so stuck at this point that I ended up referencing x2ric’s article to see what I did wrong. It turns out that we should have also tried to connect as root as the password was reused there as well.

This felt a little frustrating but the lesson here is clear. I was in the mindset of a CTF and thought I wasn’t going to be dealing with root yet since I still had two flags to go. But really I should have tried it just in case. The password reuse we already saw was probably a hint in that direction. Either way, fun room. Let’s grab our flags and go.