004#:THM - TShark Challenge I: Teamwork

Today we are going to knock out the quick TryHackMe room, TShark Challenge I: Teamwork. I’ve used Wireshark plenty but I don’t have any experience with TShark. Honestly, when I went through this room I just used grep to search the pcap file for just about everything I needed. While that is in the spirit of hacking, it isn’t in the spirit of learning so I will do it correctly for this article.
The premise for this room is that the threat research team discovered a concerning domain and has provided us with a packet capture to analyze. They suggest the only tools needed are Tshark and VirusTotal. The flags we will be looking for are the malicious URL as well as questions about the domain we can gather through OSINT.
Since we are going to do this the right way and I don’t know how to use tshark, I will just begin by looking over the help documentation.
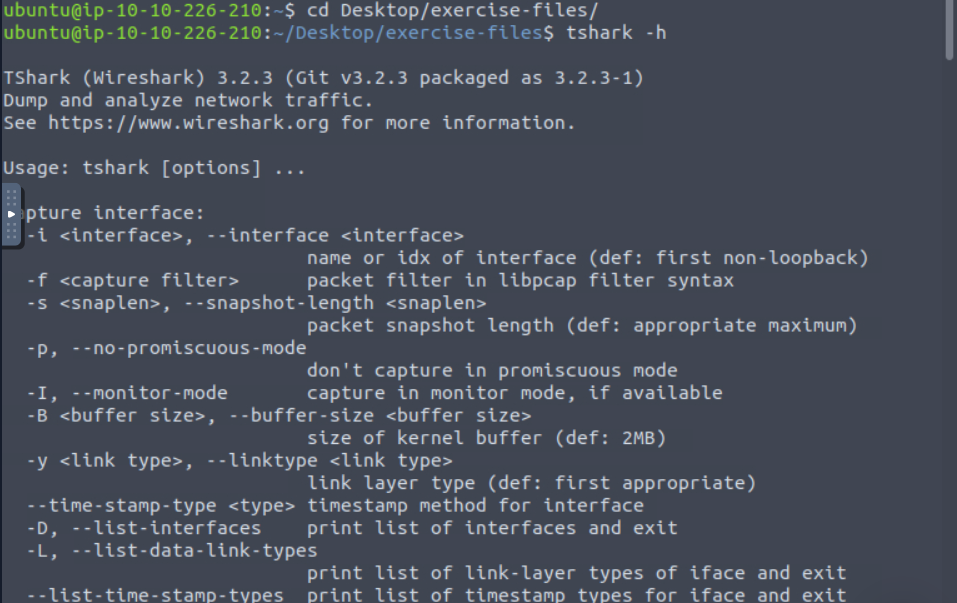
Scrolling through, it looks like we will use the -r switch to define an input file and maybe the -J switch to filter by http traffic. Let’s give it a shot. This did list the site but there was still a lot of noise in the results. Let’s try to find a tighter filter for this. Tried again but with the -Y switch instead.
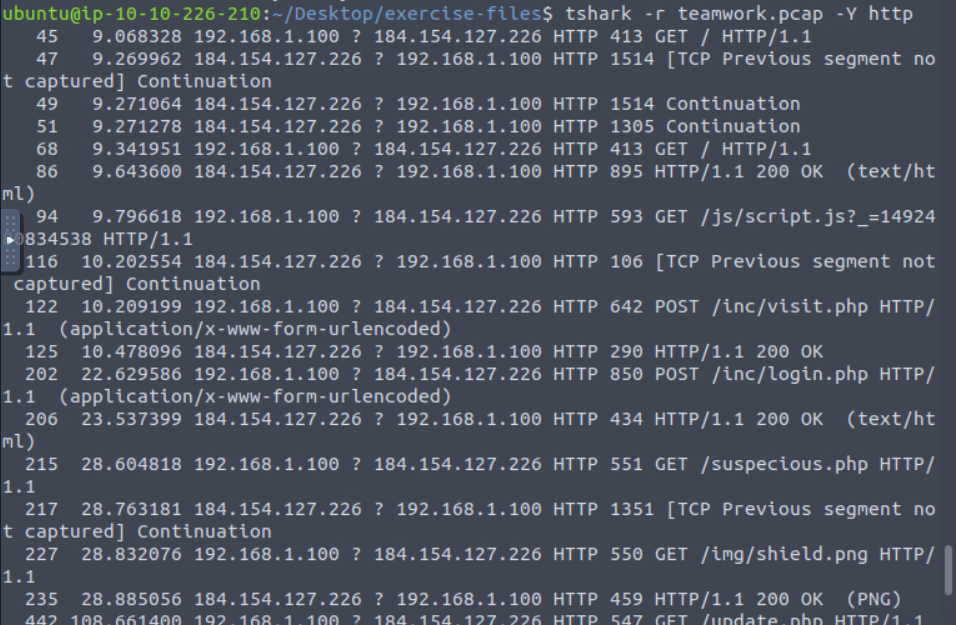
Alright, that is much better. Looking through the results we spot one address that looks obviously scamy.
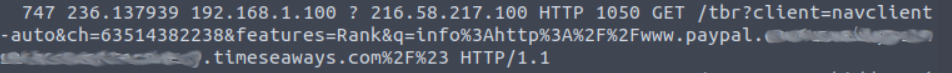
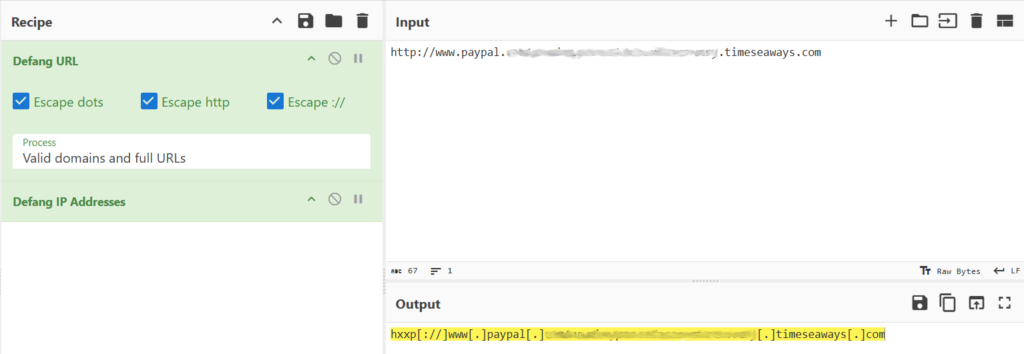
This happens to be our first flag, but we need to defang the URL first. Hop over to CyberChef and apply the Defang URL filter to the link to get our first flag.
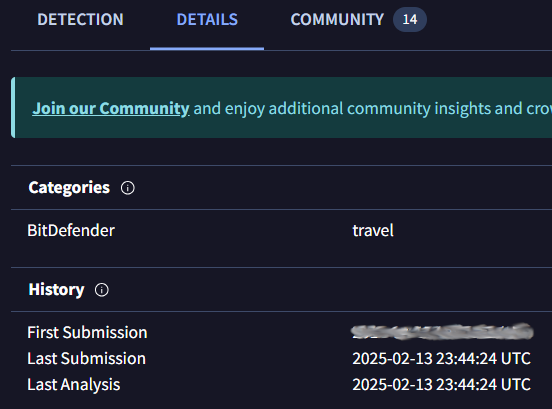
The next question has us looking this site up on VirusTotal. Under the details tab we find our second flag. Flag three can be deduced by just looking at the URL. The next flag wasn’t immediately available though. I had originally included the http:// in the beginning and the / at the end of my VirusTotal query but removing it resulted in more data on the site. Now under the Relations tab we can find the third flag.
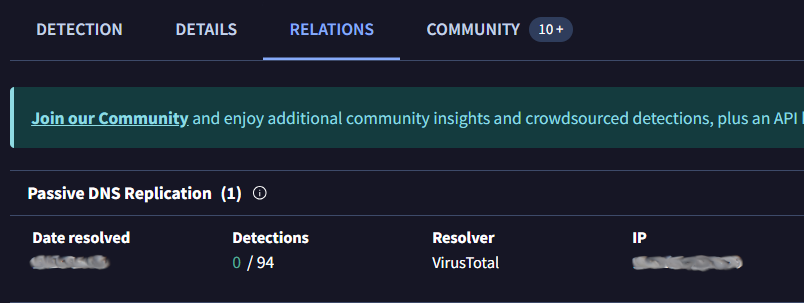
This also needs to be defanged in CyberChef, this time with the Defang IP Addresses filter applied. I tried the email address we see as the final flag but that isn’t correct. I suspect we may need to check our pcap again. I originally piped just the normal output of teamwork.pcap to grep but it didn’t get results. Checking over the help options for TShark again I see that we need the -V switch if we want the output to include the packet details. Piping it through grep to look for the use of the @ symbol predictably returned a lot of hexidecimal but also our final flag!
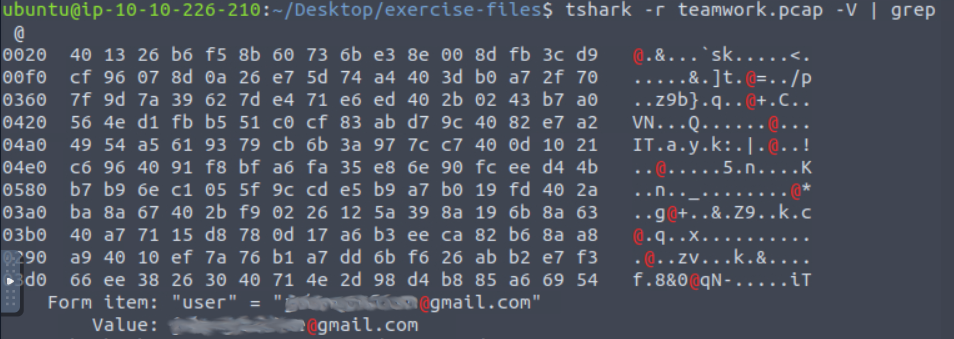
We still have to defang the email address and CyberChef doesn’t have a filter for this, but they show us how to format our final flag. With that the room is complete.
[CATZ….HACKS]